Update, 5/13/2016:
Our colleagues at Kaspersky Labs have already released an update to their free decryption tool that covers the latest version of CryptXXX described in this blog post. As usual, though, the best solution for ransomware is to avoid infection in the first place. Up-to-date network and endpoint protection, fully patched systems and software, and care when opening emails and attachments are all important components of a sound security strategy for businesses and consumers.
Overview
In mid-April, Proofpoint researchers discovered CryptXXX, a new malware variant developed by the authors of the Reveton malware and closely tied to Angler and Bedep [1]. Our colleagues at Kaspersky quickly released a decryption tool with which infected users could recover encrypted files without paying the CryptXXX ransom. However, the latest version of CryptXXX, which appeared in the wild today, renders that tool ineffective, returning the focus on CryptXXX to detection and prevention.
Analysis
CryptXXX [1] is being actively maintained: we have seen it evolve multiple times since our initial discovery, but the changes did not appear significant enough to be mentioned. As expected, the number of actors spreading it has increased, making it one of the most commonly seen ransomware families. Globally, we have observed several primary threat actors transitioning from Teslacrypt/Locky to CryptXXX/Cerber in the driveby landscape in recent weeks. CryptXXX is most frequently dropped by Bedep after Angler infection, but we have seen it dropped directly by Angler as well:
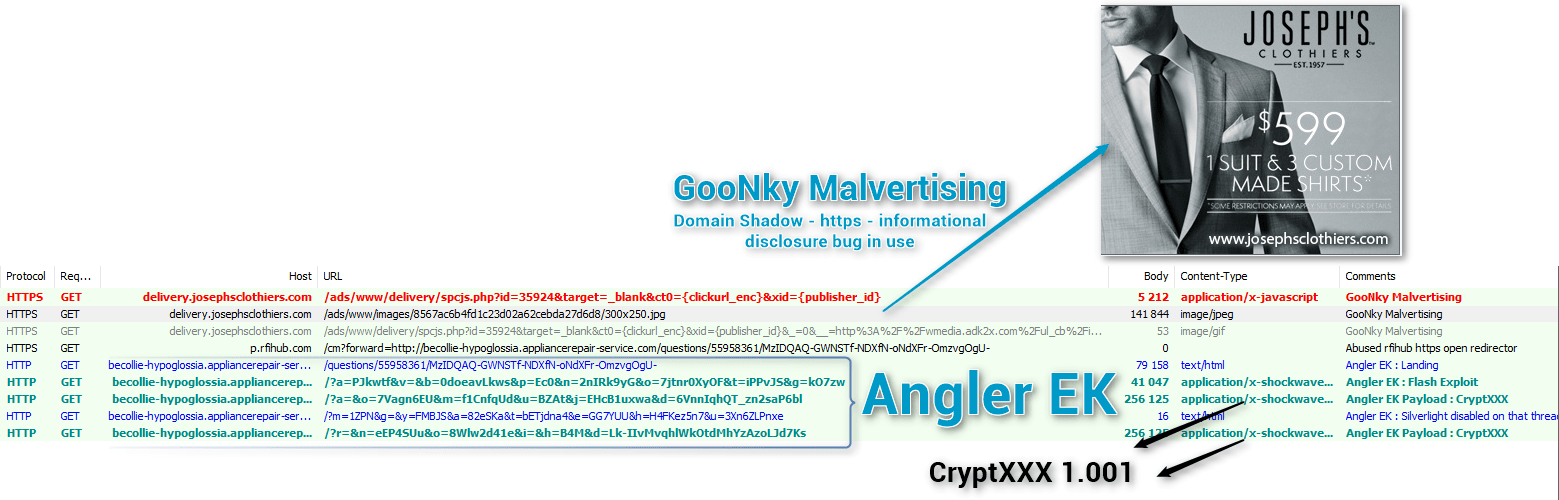
Figure 1: 2016-05-05 - Malvertising from the group we named GooNky [2] [3] leading to Angler EK dropping CryptXXX directly - Note the new https open redirector they are using.
On April 28th we observed an interesting behavior change in CryptXXX version 2.000. This version began copying the legitimate rundll32.exe file into temporary folder and renaming it there as svchost.exe. This renamed rundll32 is then used to call the original CryptXXX process with a different entry function, MS111.
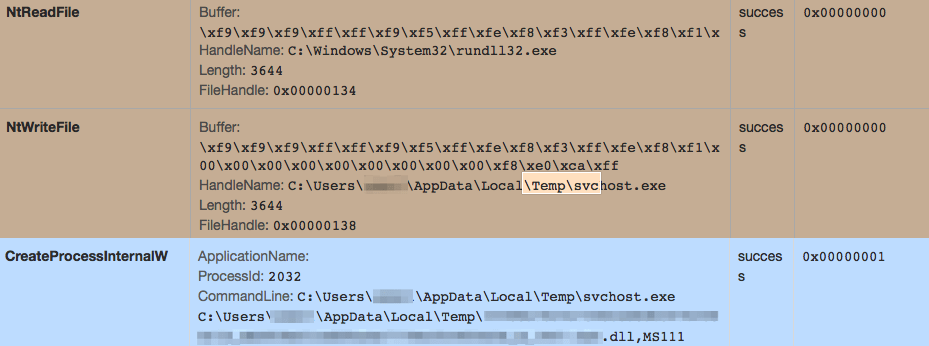
Figure 2: rundll32.exe is copied into the temporary folder and used to start the original CryptXXX DLL with a different entry function, MS111
However, the biggest modification appeared today with the version 2.006. The ransomware is now locking the screen and making the infected computer unusable.
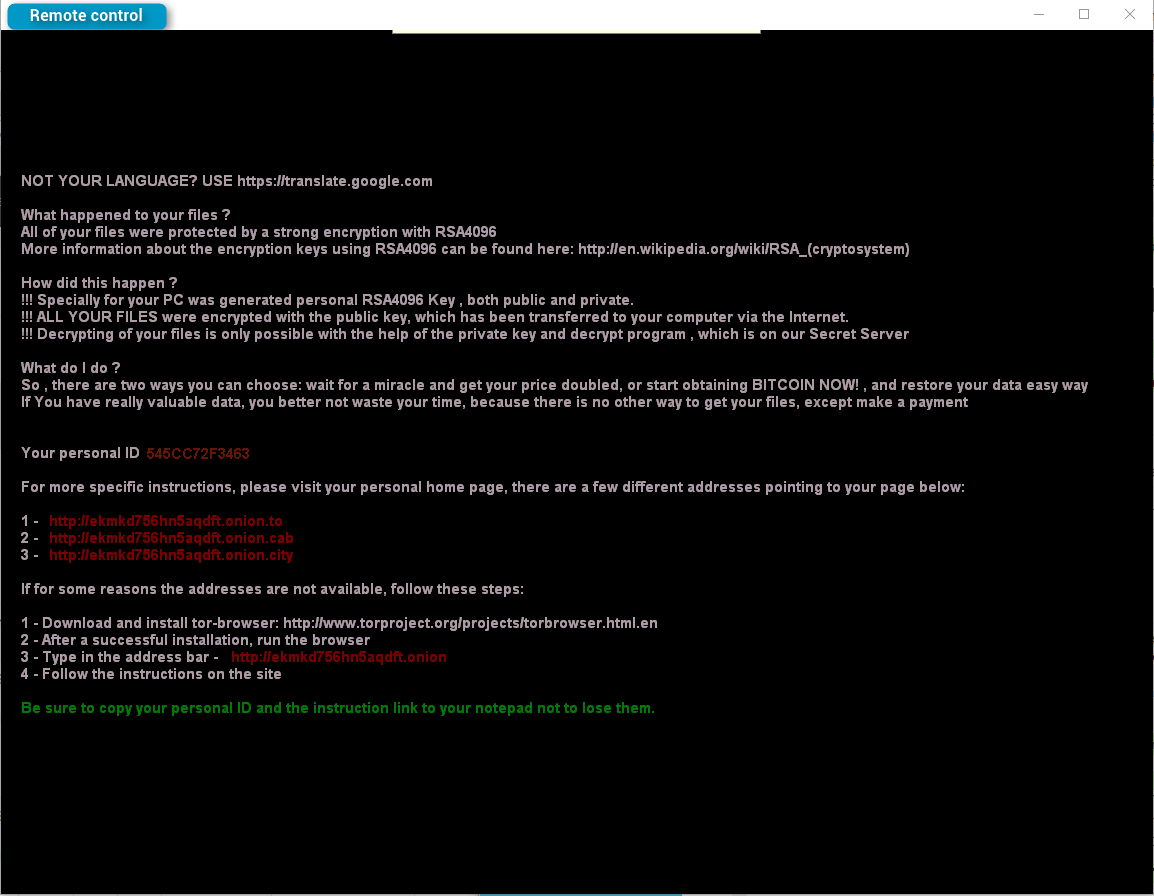
Figure 3: CryptXXX 2.006 denying access to the system with a lock screen (there is no link as no user interaction is expected from this screen)
We have not confirmed that a payment via the "personal home page" referenced above will unlock the screen. However, based on Reveton “Police locker” history (as noted previously, the authors responsible for CryptXXX were also behind Reveton), we expect this is an included feature in the ransomware, meaning the computer is probably contacting the C&C routinely to check the payment status.
We first thought that the new lock screen was a quick and dirty way to make it more difficult for the victim to use the Kaspersky decryption tool [4]. But upon further inspection, we found that the authors discovered a way to bypass the latest version of the decryption tool.
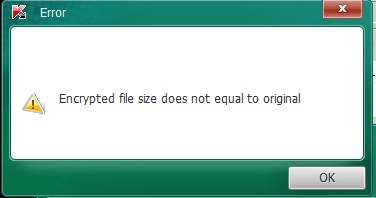
Figure 4: CryptXXX 2.006 evolution making the latest implementation of the Rannoh Decryption Tool [4] ineffective. Note that it appears that CryptXXX 2.006 is embedding zlib 1.2.2, possibly in order to defeat the current decryption tool.
The files that alert the victim that they are infected were previously “de_crypt_readme” with bmp, txt, and html extensions. These files are no longer used; instead the filenames are the unique “Personal ID” from the infected machines:
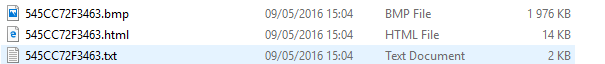
Figure 5 : Ransom message is now unique to each victim (12 hexadecimal characters)
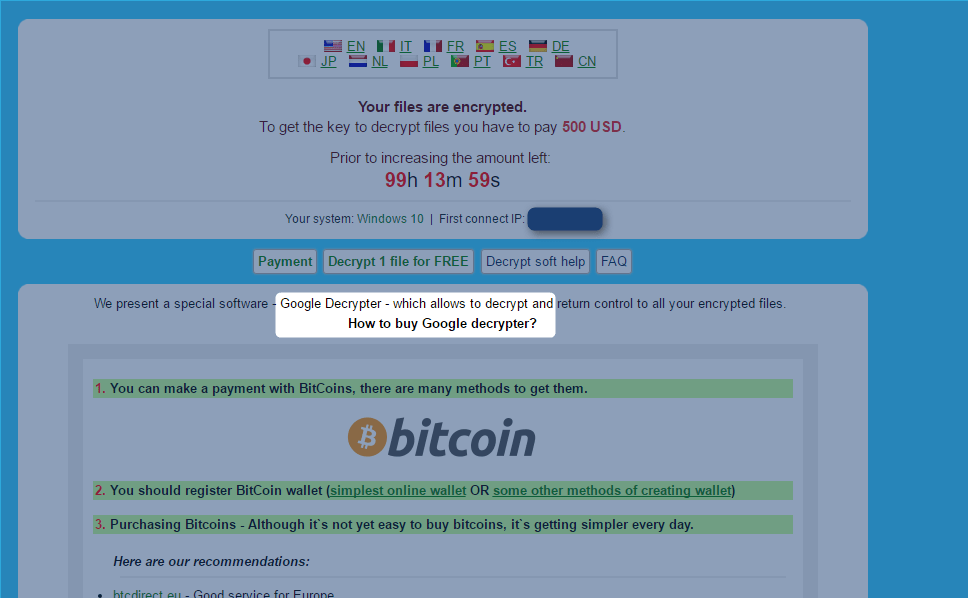
A small modification has been made on the payment page as well:
Figure 6: They now refer to “Google Decrypter” on the payment page instead of “Cryptowall Decrypter” [1]...probably to make it more difficult for victims to identify what they are facing
Conclusion
CryptXXX is rapidly emerging as one of the top ransomware families in the wild, especially among actors working primarily via exploit kits. (For its part, Locky [5] remains the top ransomware distributed via email.) With the introduction of version 2.006, CryptXXX authors have, for now, rendered the existing free decryption tool ineffective. While new decryption tools may emerge, CryptXXX's active development and rapid evolution suggest that this new ransomware will continue to compete strongly in malware ecosystems. As always, best practices for avoiding infection include patching systems and software, updating endpoint antimalware, deploying robust network protections, and regularly backing up all critical systems.
References
- https://www.proofpoint.com/us/threat-insight/post/cryptxxx-new-ransomware-actors-behind-reveton-dropping-angler
- https://www.proofpoint.com/us/threat-insight/post/The-Shadow-Knows
- https://www.proofpoint.com/us/threat-insight/post/video-malvertising-bringing-new-risks-high-profile-sites
- http://support.kaspersky.com/viruses/disinfection/8547#block1
- https://www.proofpoint.com/us/threat-insight/post/Locky-Ransomware-Cybercriminals-Introduce-New-RockLoader-Malware
Indicators of Compromise (IOC)
| IP/Domain | Comment |
|---|---|
| 217.23.13.153 | CryptXXX checkin server |
|
md5 |
sha256 |
Comment |
|
7ee094e1fb179f7ecbc39d455bdcaaf8 |
b586f73dae9e514ed62cebcd7109380103c88a15f846edcd1f4de2721d8dadd5 |
Zip archive with the 4 following samples |
|
bf322a84835c015b71d6ef90f36e8a90 |
ebff92e56c3d54f36193179f86258656ca3a7679f52d0288ae0ba2fac06a466f |
CryptXXX 1.001 |
|
e46c7530f475e07bef1a87df3c14f9d6 |
f209f9309ee9a5e2385df4957c2be4cef3ed646f34ec31b0f8035fd30ef4b95a |
CryptXXX 2.000 |
|
cf892c22f1b8cbdd33c11cc9050d483b |
21fa8ae85c1d885d82a8c4e8c4545ed64d25d28cfe2b554627fc20d79dd98c6c |
CryptXXX 2.005 |
|
22288a76cfa7348ced6db347b2085f18 |
923de3ca1ccc9bd8e50a77a43d35392febbe80832841d99857c45208c48b7d40 |
CryptXXX 2.006 |
ET Signatures that would fire on CryptXXX traffic:
2820097 || ETPRO TROJAN CryptXXX Checkin 2
2819805 || ETPRO TROJAN CryptXXX Ransomware Checkin
2819806 || ETPRO TROJAN CryptXXX Possible Payment Page