This article is more than 1 year old
Russian hackers and Britney Spears in one story. Are you OK, Reg?
We're fine. You might not be as Turla espionage-ware uses Britney's Instagram for evil
The malware scum behind the ongoing Turla campaign have been spotted experimenting with Instagram accounts as a C&C channel.
The Russian-sourced (and allegedly state-backed) Turla espionage tool has repeatedly re-emerged since its discovery in 2014.
ESET has turned up a Firefox extension that implements a simple backdoor on Windows targets.
At this stage, the company's Jean-Ian Boutin writes, it looks like a test run for something the vxers hope to deploy in the future: the malware is collecting info about targets, encrypting it with AES, and sending it to a C&C server.
What's clickbaity interesting about this is how the extension gets the address of its C&C: in the test run, it was posted to comments to Britney Spears' Instagram account.
“The extension will look at each photo’s comment and will compute a custom hash value”, ESET explains.
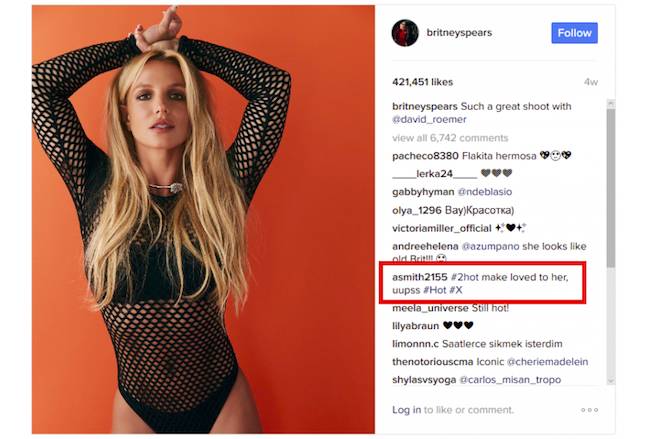
The right comment hashes to give attackers the C&C address
The magic number is 183: if the hash matches, the comment is parsed with regex to get the C&C's Bitly-shortened URL.
Apparently, the idea is to use the February test run of the infected Firefox extension (ESET says it first saw the malware on an unnamed, compromised Swiss security company) to prepare something more effective for the future. ®
