
Many brands of webcams, security cameras, pet and baby monitors, use a woefully insecure cloud-based remote control system that can allow hackers to take over devices by performing Internet scans, modifying the device ID parameter, and using a default password to gain control over the user's equipment and its video stream.
In the last nine months, two security firms have published research on the matter. Both pieces of research detail how the camera vendor lets customers use a mobile app to control their device from remote locations and view its video stream.
The mobile app requires the user to enter a device ID, and a password found on the device's box or the device itself. Under the hood, the mobile app connects to the vendor's backend cloud server, and this server establishes connections to each of the user's device in turn, based on the device ID and the last IP address the device has reported from.
Many cameras feature silly passwords
Last year, Security Research Labs (SRLabs) published a report and gave a talk at a security conference in Berlin about this issue.
The company found that several vendors were using this "camera management scheme" but were using sequential IDs for their devices with default passwords such as "123," "123456," or "888888." The company found over 810,000 devices exposed this way.
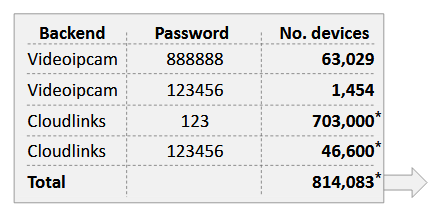
SRLabs said that because the IDs weren't randomly generated, it was trivial for an attacker to create a script that connects to the vendor's backend cloud server and attempt to add devices by cycling through the sequential device IDs and using the default password.
This simple scheme allows hackers to add hijacked cameras to their own Android apps, and interact with the camera or watch its video stream. Below is a video demonstration of such a script.
Security firm tracks real vendor behind many resellers
Yesterday, security researchers from SEC Consult published a report that analyzed the device at a recent spying scandal.
Earlier this month, a mother from South Carolina complained that a hacker took control over her baby monitor and started moving the camera around the room as she was taking care of her child. The mother posted her account of the event on Facebook, which was later picked up by several news outlets [1, 2, 3].
SEC Consult looked at the baby monitor used in that case, a FREDI pet and baby monitor, and discovered the same vulnerable management model that involved a mobile app, a remote cloud sever, and a device with sequential IDs and default password of "123."
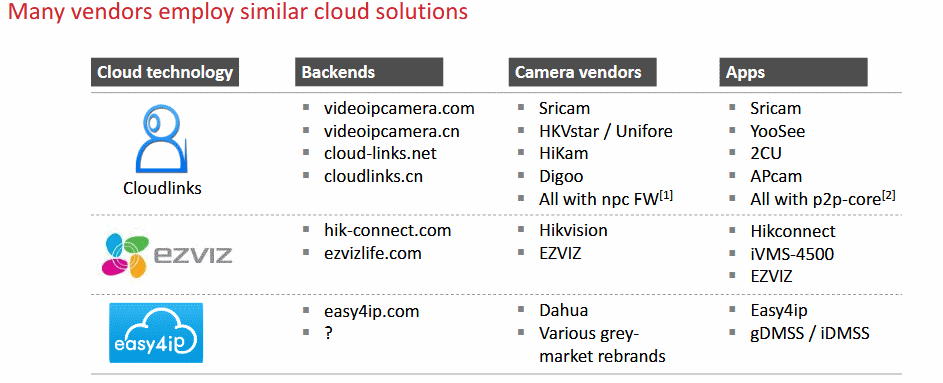
Researchers tracked the FREDI devices to a Chinese company named "Shenzhen Gwelltimes Technology Co., Ltd." They said this is a vendor of white-label security cameras and baby monitors that sells devices to other vendors across the world.
The reseller companies order entire batches of Shenzhen Gwelltimes cameras with their own brand and customized manuals, and then turn around to re-sell these cameras on Amazon or in their countries.
The privacy implications are enormous
All these rebranded devices use the same Gwelltimes cloud service and Gwelltimes app (named Yoosee) to let customers manage devices. The Yoosee app has over 1 million installs through the Google Play Store alone, meaning that millions of video streams can be easily accessible through this service.
"Obviously, the device and the cloud service is not GDPR compliant," SEC Consult said. "Here we have a Chinese company that is never mentioned anywhere, developing insecure products and sending our most private information home to their Chinese servers."
This is a classic case of a supply-chain vulnerability —when the vendor of a product is not actual the product's real manufacturer— something the US is trying to address in recently proposed legislation.
SEC Consult believes that Shenzhen Gwelltimes Technology is also one of the vendors behind the security camera models that SRLabs analyzed last year, as YooSee was listed as an app used for controlling Cloudlinks and Videoipcamera devices. These two camera brands are most likely Shenzhen Gwelltimes devices, rebranded and resold by their respective owners.
"Although they have been confronted with the security issues months ago, they have decided not to fix them," SEC Consult said about the fact that Shenzhen Gwelltimes didn't appear to change anything in its products following the publication of the SRLabs report.
At least one hacker is taking over cameras
"In the South Carolina case the most likely scenario is that someone is scanning for valid device IDs with insecure/default passwords and then spies on the owners of the device, possibly based on the information released by Security Research Labs in November 2017," researchers said.
If your smart home camera, pet and baby monitor involve installing the Yoosee app, then you're most likely affected by this issue, and your device might be easily taken over by nosey hackers.
To stay protected, security researchers advise owners of such devices to use the YooSee app and change the device's default password, as the app allows this from its interface, right after adding a new device.



Comments
cbaksa - 5 years ago
Where as this practice of a Product Gateway allows the vendor to deliver a product that is plug and play, it opens a ton of security holes. The average users does not understand how this functions, they only see the ease of use and the vendor benefits by skirting around having to support difficult firewall settings on a plethora of Routers. The very 1st thing I do when I buy a camera is assign it a static IP address, change the default password and Block it with a firewall rule from being able to communicate outside of my internal network. This way the camera can't communicate with the Product Gateway and establish a link.