The scourge of the remote access trojan (RAT)—those predatory apps that use Web microphones and cameras to surreptitiously spy on victims—has formally entered the Android arena. Not only have researchers found a covert RAT briefly available for download in the official Google Play store, they have also detected a full-featured toolkit for sale in underground forums that could make it easy for other peeping Toms to do the same thing.
The specific RAT in Google Play was disguised as a legitimate app called Parental Control, according to Marc Rogers, principal security researcher at Lookout Mobile, a provider of antimalware software for Android phones. He doesn't know exactly how long it was available on Google servers, but he believes it wasn't long. It was downloaded 10 to 50 times.
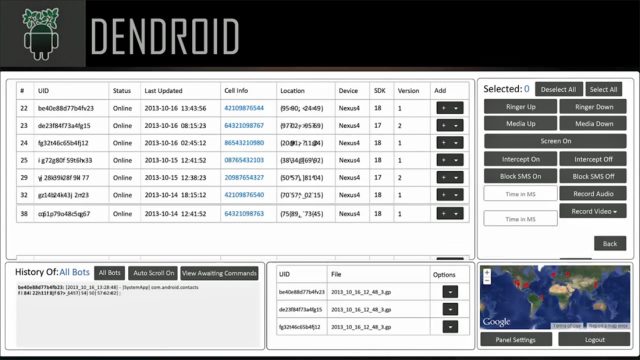
The Parental Control trojan was built using Dendroid, a newly discovered software development tool that sells for about $300. Dendroid provides an impressive suite of features, including all the tools to build the command and control infrastructure to control RATted phones and receive audio and video captured from their mics and cameras. Dendroid also allows attackers to intercept, block, or send SMS text messages on compromised phones; download stored pictures and browser histories; and open a dialogue box that asks for passwords. It includes "binder" functions that allow the malicious code to be attached, or bound, into otherwise useful or innocuous apps.
Dendroid also gives apps the ability to evade Bouncer, Google's cloud-based service that scours the Android Market for malicious apps. Dendroid apps do this by including code that defeats "emulation" code Bouncer uses to log and understand the behavior of the apps it's analyzing. Dendroid's anti-emulation capabilities prevent apps from carrying out any suspicious or nefarious activities during the Bouncer scan, allowing them to evade its watchful eye.
In a blog post, Lookout's Rogers continued:
This toolkit is different from the majority of custom Android malware solutions in other ways as well. Most of these solutions typically just offer a few pieces of code for the wannabe malware author to insert into an innocent target application. More sophisticated features, such as command and control of infected devices, is then left up to the operator to implement. Dendroid, on the other hand, offers a full command and control infrastructure with a control panel every bit as feature rich as some of the more sophisticated Russian botnets.
Rogers told Ars that he downloaded the Parental Control app and identified it as containing the DNA of the Dendroid toolkit. In tests, the app ran without crashing and appeared to do what it was supposed to do, including connecting to the control servers it was configured to talk to, all without any overt signs what was happening.
In Google's defense, the company does a good job catching malicious titles submitted to the Play store, and in the event of misses, it quickly removes trojans as soon as they become known. With no more than 50 downloads of Parental Control, it's possible that the app had few, if any, victims. Google also endows Android phones with the ability to be purged of installed apps that are later discovered to be harmful.
That said, the instance of Google's official Play Store hosting malicious apps is a regular occurrence that should make people think twice about trusting specific apps, especially those that are relatively new haven't been downloaded many times. It's unclear if Parental Control did everything the purveyors of Dendroid advertise. The fact that an app on Google servers contained the Dendroid-spawned code and connected to suspicious control servers should be enough to give users pause.
Listing image by Aurich Lawson / Thinkstock
reader comments
100