A day after security Kaspersky Lab researchers detailed a state-sponsored hacking campaign with ties to Stuxnet, an online posting has been spotted in which one of the victims pleaded for help.
"How do I stop this virus infecting my computer?" someone with the username dkk wrote in a forum in July 2010. "You insert the USB thumbdrive, the computer gets infected. Even when the patches has been applied, and autorun and autoplay has been turned off. The weirdest thing of all is, there is in fact no autorun.inf on the root of the infected USB drive."
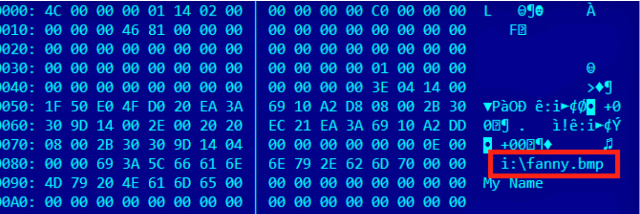
He went on to say the USB drive contained seven files all ending in *.lnk, along with a file called fanny.bmp. Sadly, no one ever responded.
It wasn't until Monday, more than four years after dkk posted his plea for help, that it became public knowledge that highly advanced state-sponsored hackers used a USB-based computer worm as part of a 14-year espionage campaign that may have infected tens of thousands of people. One attack exploited what was then a zero-day vulnerability in Windows functions that process so-called .LNK files used to display icons when a USB stick is connected. By embedding malicious code inside the .LNK files, a booby-trapped stick could automatically infect the connected computer even when its autorun feature was turned off. Kaspersky Lab researchers dubbed the self-replicating exploit Fanny because one of the booby-trapped files it used was titled fanny.bmp.Costin Raiu, director of Kaspersky Lab's global research and analysis team, told Ars the files described in the post are consistent with the Fanny infections developed by Equation Group, the name Kaspersky has given to the hacking crew.
According to journalist and author Kim Zetter's Countdown to Zero Day: Stuxnet and the Launch of the World's First Digital Weapon, the .LNK vulnerability was first publicly disclosed on July 12, 2010, one day prior to dkk's July 13 post. It was posted by the Wilders Security forum on VirusBlokAda. A few days later, security journalist Brian Krebs reported on it. It was around this time that antivirus providers updated their products to detect .LNK exploits. Microsoft patched the vulnerability in August, 2010. According to Kaspersky, the zero-day was first used in Fanny in 2008 and added to Stuxnet two years later.
Dkk's request was posted to a forum on Lowyat.net, which bills itself as Malaysia's largest online community. It makes sense that dkk's post appeared on a site frequented by Malaysians. According to Kaspersky, Malaysia was one of 30 countries whose residents are known to have been infected by Equation Group malware.
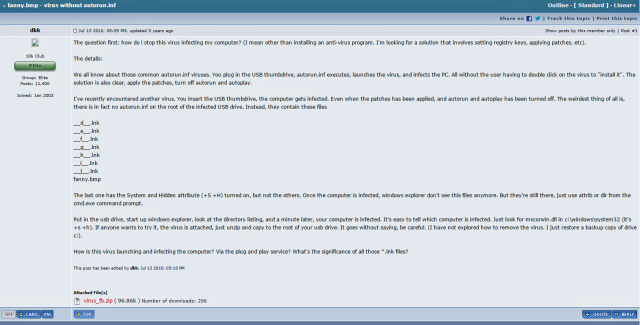
We don't know how things turned out for dkk. The user has made 11,400 posts, with the most recent one in November. The link to dkk's post was tweeted earlier by Maarten van Dantzig, a security researcher at Fox-IT.
reader comments
88