Update: Late Friday afternoon, Apple officials released the following statement: "Earlier this week we implemented a server-side app security update that secures app data and blocks apps with sandbox configuration issues from the Mac App Store. We have additional fixes in progress and are working with the researchers to investigate the claims in their paper."
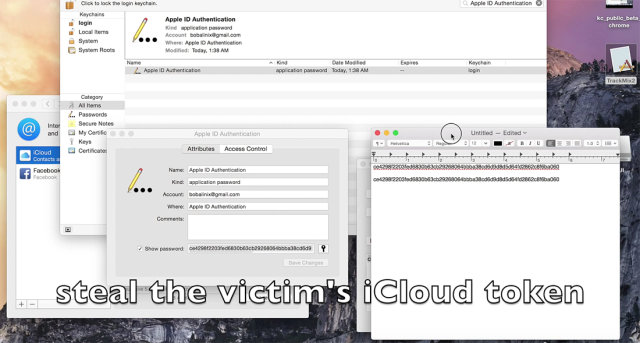
Researchers have uncovered huge holes in the application sandboxes protecting Apple's OS X and iOS operating systems, a discovery that allows them to create apps that pilfer iCloud, Gmail, and banking passwords and can also siphon data from 1Password, Evernote, and other apps.
The malicious proof-of-concept apps were approved by the Apple Store, which requires all qualifying submissions to treat every other app as untrusted. Despite the supposed vetting by Apple engineers, the researchers' apps were able to bypass sandboxing protections that are supposed to prevent one app from accessing the credentials, contacts, and other resources belonging to another app. Like Linux, Android, Windows, and most other mainstream OSes, OS X and iOS strictly limit app access for the purpose of protecting them against malware. The success of the researchers' cross-app resource access—or XARA—attacks, raises troubling doubts about those assurances on the widely used Apple platforms.
"The consequences are dire," they wrote in a research paper titled Unauthorized Cross-App Resource Access on MAC OS X and iOS. "For example, on the latest Mac OS X 10.10.3, our sandboxed app successfully retrieved from the system's keychain the passwords and secret tokens of iCloud, email and all kinds of social networks stored there by the system app Internet Accounts, and bank and Gmail passwords from Google Chrome." Referring to interprocess communication, which is the tightly controlled and Apple-approved mechanism for one app to interact with another and the Bundle ID token used to enforce sandbox policies, the researchers continued:
From various IPC channels, we intercepted user passwords maintained by the popular 1Password app (ranked 3rd by the MAC App Store) and the secret token of Evernote (ranked 3rd in the free “Productivity” apps); also, through exploiting the BID vulnerability, our app collected all the private notes under Evernote and all the photos under WeChat. We reported our findings to Apple and other software vendors, who all acknowledged their importance. We also built an app that captures the attempts to exploit the weaknesses.
A brief history of sandboxing
The Apple sandbox made its debut in OS X and uses the mandatory access control framework from the TrustedBSD project to enforce security policies at the system-call level. Since version 10.7.5, most apps submitted to Apple's Mac App Store are required to adhere to the sandboxing scheme. By default, the OS X Gatekeeper prevents users from installing apps unless they come from the store or come from a trusted developer that adheres to sandboxing requirements. iOS apps, meanwhile, have always adhered to strict sandboxing.
Despite the strict controls, the researchers found several ways a malicious app can surreptitiously access data from another app that's supposed to be off-limits. They included:
IPC interception: Browsers and other Internet-connected apps often use the WebSocket protocol to interact with extensions or other apps. Malicious apps can capitalize on this usage by preemptively taking control of the Internet port a trusted app uses to send or receive data through the WebSocket channel. The researchers wrote:
The security risks of intercepting the IPC communication through these vulnerable channels are realistic and serious. As an example, here we just elaborate our end-to-end attacks on three popular apps. We analyzed the 1Password app for OS X, which is one of the most popular password management apps and ranked 3rd by the MAC App Store. The app comes with a browser extension for each major browser that collects the passwords from the user’s web account and passes them to the app through a WebSocket connection. In our research, our sandboxed app created a local WebSocket server that took over the port 6263, before the 1Password app did, and was successfully connected to the password extension and downloaded the password whenever the user logged into her web account. We reported our findings to the 1Password security team, which acknowledged the gravity of this problem. This attack succeeded on OS X 10.10 (latest version when we reported the problem), against Chrome, Firefox and Safari. Our attack code passed the vetting process of the MAC Store.
A video demonstration of the attack is below:
In a detailed blog post published in response to the new proof-of-concept exploit, AgileBits "Chief Defender Against the Dark Arts" Jeffrey Goldberg wrote: "The fact of the matter is that specialized malware can capture some of the information sent by the 1Password browser extension and 1Password mini on the Mac under certain circumstances. But roughly speaking, such malware can do no more (and actually considerably less) than what a malicious browser extension could do in your browser."
Goldberg, whose company develops and markets 1Password, went on to advise users how to make themselves less susceptible to the attack and to thank the researchers for exposing the problem.
Password stealing is when a malicious app exploits a subtle design weakness in the OS X keychain, which stores passwords and other credentials used by browsers and other apps. By design, an individual keychain item is supposed to be available only to the app that originally added it, unless exceptions are explicitly approved. A malicious app can secretly allocate keychain attributes for apps that have not yet been installed in hopes the user will install them later. If the bet pans out, the malicious app will have full access to the credentials. In the case the malicious app is installed after a targeted trusted app is already in place, the malicious app can simply delete the password. Once the end user enters it again, the malicious app will be able to retrieve it.
A video demonstration of the attack follows:
Container cracking: Containers are designed to store the contacts, passwords, and other contents in highly restricted directories and subdirectories named after the BID assigned to the sandboxed app. The Mac App Store, however, fails to verify whether the subdirectory of a legitimate app is the same as one claimed by a malicious app.
"Once the attack app is launched, whenever the OS finds out that the container directory bearing the sub-target's BID (as its name) already exists, the sub-target is automatically added onto the directory's ACL [access control list]," the researchers wrote. "As a result, the malicious app gains the full access to other apps' containers, which completely breaks its sandbox confinement."
Scheme hijacking: OS X and iOS automatically associate certain URL schemes with a particular app so it can be opened when associated data is received from an Internet-connected server. URLs beginning with wunderlist://, for instance, will open the to-do list management app by that name and pass a variety of parameters to it. The researchers' malicious app was able to take ownership of the Wunderlist URL scheme and then steal the Google Single Sign On login credential transmitted by the browser. To prevent the targeted user from discovering the attack, the app then delivered the pilfered token to Wunderlist, causing the app to behave normally.
It's not the first time researchers have found flaws in application sandboxes. The attack exploiting WebSocket weaknesses, for instance, can also succeed in Windows under certain conditions, the researchers said. Interestingly, they said application sandboxing in Google's Android OS was much better at withstanding XARA threats.
For the time being, the researchers told Ars, there isn't much end users can do except wait for Apple to fix the vulnerabilities. At the request of Apple, the researchers delayed disclosing their findings for six months to give developers a head start in hardening OS X and iOS against the attacks. Since reporting the keychain vulnerabilities to Apple, company engineers started using a random username to patch some of its apps, a countermeasure the researchers said is ultimately "futile."
In light of the vulnerabilities, users of all OSes should limit the apps they install to those that are truly needed and explicitly trusted.
"The consequences of such attacks are devastating, leading to complete disclosure of the most sensitive user information (e.g., passwords) to a malicious app even when it is sandboxed," the researchers warned. "Such findings, which we believe are just a tip of the iceberg, will certainly inspire the follow-up research on other XARA hazards across platforms."
Listing image: Simon Greig
Post updated to add comment from AgileBits.
Listing image by Simon Greig
reader comments
121