It’s been over a year since the first wave of cryptographic extortion malware hit computers. Since then, an untold number of individuals, small businesses and even local governments have been hit by various versions of malware that holds victims’ files hostage with encryption, demanding payment by Bitcoin or other e-currency in exchange for a key to reverse the damage. And while the early leader, CryptoLocker, was taken down (along with the “Gameover ZeuS” botnet) last June, other improved “ransomware” packages have sprung up to fill its niche—including the sound-alike CryptoWall.
Ransomware is a strange hybrid of digital mugging and commercial-grade coding and “customer service”—in order to continue to be able to generate cash from their malware, the criminal organizations behind them need to be able to process payments and provide victims with a way to get their files back, lest people refuse to pay because of bad word-of-mouth. And to grow their potential market, the extortionists need to find ways to make their “product” work on a wide range of potential target systems. The apex of this combination of crime and commerce is (at least so far) the latest version of CryptoWall—CryptoWall 2.0.
In a blog post this week, researchers Andrea Allievi and Earl Carter of Cisco‘s Talos Group presented a full code dissection of CryptoWall 2.0 and found a few surprises, aside from using a number of different, sophisticated features to attack systems and evade detection before it can strike. And while the malware is 32-bit Windows code to ensure the widest reach possible, it can detect when a 64-bit Windows environment is available and switch some of its functionality to run in full 64-bit native mode—ensuring it can do maximum damage on the most recent Windows client and server platforms.
Aside from the professionally written code, CryptoWall 2.0 also apparently comes backed by a professional “support” team. As essayist Alina Simone reported in a recent story for the New York Times (“How My Mom Got Hacked”), when her mother missed a deadline for making a Bitcoin payment to the CryptoWall crew because of trouble obtaining Bitcoins and fluctuations in their value—and was slammed with a doubling of the ransom for her files— she was able to talk to the ring through the malware’s messaging interface and explain her situation. The CryptoWallers responded by providing her with the decryption key. Hooray for honor among thieves.
CryptoWall 2.0, like most of the other ransomware variants, is a Windows-specific malware package—though it can run on nearly any version of Windows currently deployed. On the version tested by Talos, it exploited a known 32-bit Windows privilege elevation vulnerability (which executes in “Windows on Windows” mode in 64-bit versions of the Windows OS) to install itself. While that exploit was patched by a Microsoft security update for nearly every Windows operating system up to Windows 8 and Server 2012, other exploits can be used by other versions of the dropper. Typically, the dropper is delivered as part of an e-mail “phishing” attack, but it could also be delivered through a malicious website using an exploit kit. Some samples of CryptoWall have come in on malicious PDF files; Palo Alto Networks discovered one in a spam e-mail disguised as an "Incoming Fax Report."
Cloaking enabled
The installation components of CryptoWall 2.0 are cloaked by multiple levels of encryption, with three distinct stages of installation each using a different encryption method to disguise the components installed. And like many modern pieces of malware, CryptoWall 2.0 has a virtual machine check in its code that disables the attack when the malware is installed within a virtual instance—in part to prevent security researchers from isolating and analyzing its behavior.
The VM checker code, in the first stage of CryptoWall’s dropper sequence, checks the system for running processes, searching for VMware and VirtualBox services or the Sandboxie application partitioning library. If the coast is clear, the code does some best practices-based memory handling to release memory used in the initial drop mode, then launches another dropper disguised as a Windows Explorer process.
The second stage dropper creates a uniquely named version of the main CryptoWall installation code based on an MD5 hash of the computer’s name and installs auto-run registry entries for the executable so that it will restart, including one that ensures that it will start even if the computer is rebooted in “safe mode.”
The dropper also runs a few shell commands to turn off things that might protect the system from the next phase of the malware’s attack—using Windows’ Vssadmin command to turn off “shadow copy” snapshots of files and disk volumes and BCDEdit to change boot configuration on the system to turn off system recovery features. And it turns off Windows’ Security Center, Windows Defender, Windows Update, error reporting, and a few other services to clear the path for the final malware countdown.
The final installation routine for CryptoWall shows up in Windows’ Task Manager as a “svchost.exe” process. It reaches out to a series of malicious web pages in an attempt to download a Tor client component used to conceal communications with CryptoWall’s command and control (C&C) network from one of a series of hard-coded URLs associated with compromised websites—many of them apparently WordPress blogs on hosts that have been used as repositories for the file, which has been triple-encrypted. Once the Tor communications module has been extracted and launched, CryptoWall 2.0 generates random custom Tor addresses to use to direct the victim.
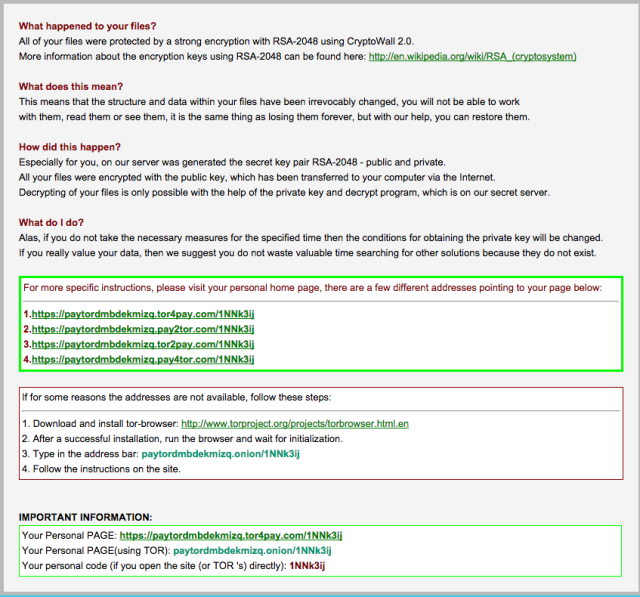
And then there's the encryption. CryptoWall uses 2,048-bit RSA encryption, using a public key retrieved from the CryptoWall C&C network. The private key required to decrypt the files stays on the server until the victim pays up.
From Russia, with spite
The servers that host the sites generated for victims to submit their payments on the version of CryptoWall analyzed by Talos were all hosted within the domains tor2pay.com and tor4pay.com—domains that Ars found were registered in Russia to a Sergey Svalkin in Moscow, with the e-mail address ladomfichisi1987@mail.ru. (Ironically, Sergey Svalkin is the name of the warden of Correction Colony 13, a prison for policemen, judges, and others involved in law enforcement who have been convicted for corruption or brutality.) The domains all resolve to a single IP address in Russia.
There is some telltale traffic generated by the CyberWall infection. First of all, it tries to determine the Internet-facing IP address for the infected system by sending requests to a number of websites that allow users to identify their IP address if they are inside a network address translation firewall. The first on the list is wtfismyip.com—which “shouldn’t be a very common occurrence in an enterprise network,” Allievi and Carter said. And while the SSH connections from CryptoWall use random server names in their certificates, those names have enough commonality to be detected—and they will show up as a large amount of unusual traffic.
As CryptoWall becomes more well-known, it will also become harder for the people behind it to successfully infect new victims. Mail filters that block phishing e-mails and application firewalls that use rules to block traffic to suspicious or known malicious websites with rules updated to catch CryptoWall before it can fully install will protect many enterprises. But individuals running older versions of Windows without good spam filtering and malware protection will continue to be at risk for some time. And given how much effort the people behind CryptoWall have put into this new release, there’s sure to be another one dropping some time soon to leapfrog malware detection systems again.
Listing image by Aram Bartholl. Dead Drops
reader comments
282