It's still not clear how, but a disproportionately large number of websites that run on the WordPress content management system are being hacked to deliver crypto ransomware and other malicious software to unwitting end users.
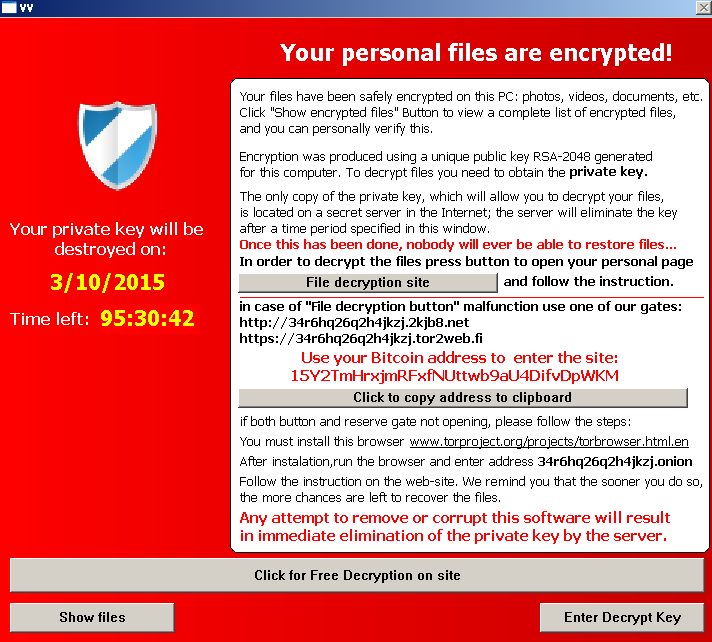
In the past four days, researchers from three separate security firms have reported that a large number of legitimate WordPress sites have been hacked to silently redirect visitors to a series of malicious sites. The attack sites host code from the Nuclear exploit kit that's available for sale in black markets across the Internet. People who visit the WordPress sites using out-of-date versions of Adobe Flash Player, Adobe Reader, Microsoft Silverlight, or Internet Explorer can then find their computers infected with the Teslacrypt ransomware package, which encrypts user files and demands a hefty ransom for the decryption key needed to restore them.
"WordPress sites are injected with huge blurbs of rogue code that perform a silent redirection to domains appearing to be hosting ads," Malwarebytes Senior Security Researcher Jérôme Segura wrote in a blog post published Wednesday. "This is a distraction (and fraud) as the ad is stuffed with more code that sends visitors to the Nuclear Exploit Kit."
According to a Monday blog post published by website security firm Sucuri, the compromised WordPress sites he observed have been hacked to include encrypted code at the end of all legitimate JavaScript files. The encrypted content is different from site to site, but once decrypted, it looks similar to that shown in the image below:
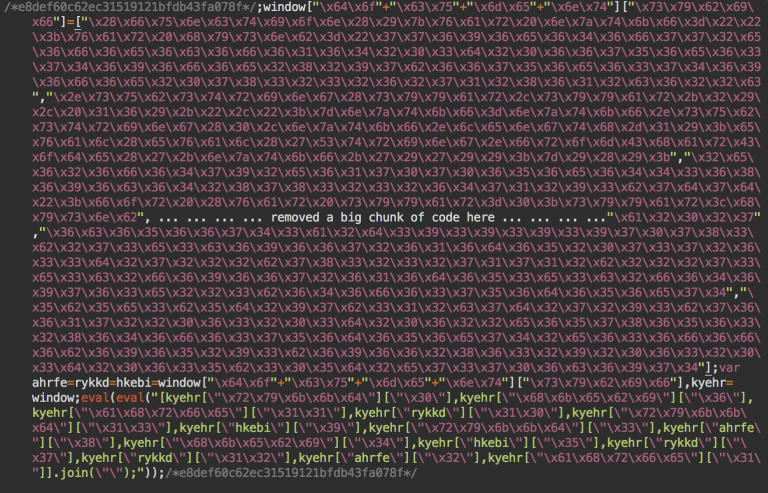
To prevent detection by researchers visiting the compromised site, the code takes pains to infect only first-time visitors. To further conceal the attack, the code redirects end users through a series of sites before delivering the final, malicious payload. Sucuri said Google's Safe Browsing mechanism—which browser makers use to help users avoid malicious websites—had blacklisted some of the Internet domains used in the ruse. A post published Thursday by Heimdal Security, however, listed a different domain, leaving open the possibility that the attackers are regularly refreshing as old ones get flagged.

 Loading comments...
Loading comments...
