
While we were researching the malicious program Lurk in early February 2016, we discovered an interesting oddity in how this banking Trojan spreads. From the data we had, it emerged that the users attacked by Lurk also installed the remote administration software Ammyy Admin on their computers. At first, we didn’t really give this much thought, but further research showed that the official Ammyy Admin website had most probably been compromised, and the Trojan had been downloaded to users’ computers along with the legitimate Ammyy Admin software.
It turned out that on the official site of Ammyy Admin (which is used for remote desktop access) there was an installer that did not have a digital signature and was an NSIS archive. When this archive was launched, two files were created in a temporary folder and launched for execution:
- aa_v3.exe – installer of the administration tool Ammyy Admin, signed with a digital signature;
- ammyysvc.exe – malicious spyware program Trojan-Spy.Win32.Lurk.
In other words, the Ammyy Admin installer available for download on the manufacturer’s official website is basically a dropper Trojan designed to stealthily install a malicious program in the system, while displaying a screen mimicking the installation of legitimate software. We found out that the dropper was being distributed on a regular basis (with short breaks) over several hours on weekdays.
Last November other researchers wrote about this same method of distributing malware, however that publication did not stop the distribution of the Trojan.
Official Ammyy Admin website. Note the ‘Download’ button
By the way, some browsers (e.g. Mozilla Firefox) were flagging the www.ammyy.com website as potentially dangerous at the time of writing this post, and warning about the presence of unwanted software.

Mozilla Firefox warning page displayed when an attempt is made to access www.ammyy.com
To ensure successful distribution of the malicious program, the cybercriminals modified the PHP script on the Ammyy Group web server in such a way that the malicious dropper was provided when a download request was made.
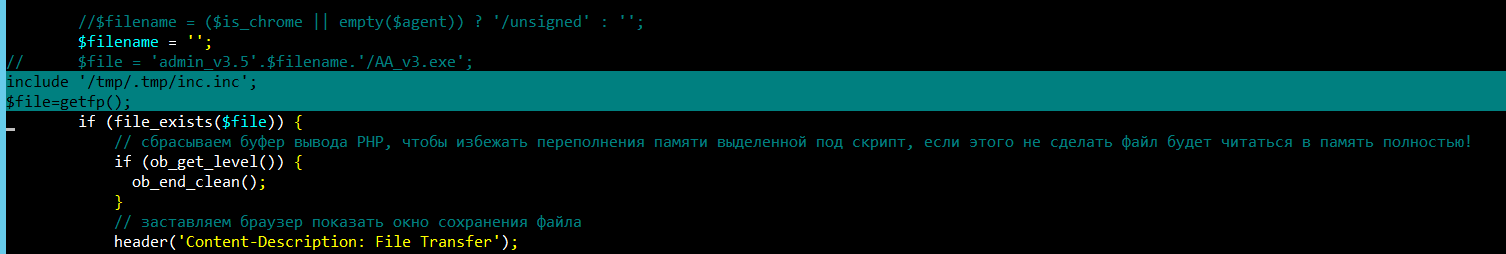
An external function was added to the PHP script on the web server
In early April, the cybercriminals uploaded a new, slightly modified dropper for distribution. At launch, it used the function GetComputerNameExA to check if the computer being infected was part of a corporate network; if so, it launched the Lurk malicious program along with the remote administration tool. This shows that the cybercriminals were specifically hunting for corporate workstations and servers.
We should note that attacks of this type (Watering Hole) are very effective, and doubly dangerous if they target the users of a remote administration software tool: administrators using such a tool might presume that a malware (or malicious activity) detection event reported by their security software is a false positive triggered by the presence of the remote administration tool itself, and allow the detected activity. Moreover, they could disable protection or add the malicious program to the tracking and checking exemption list, thus allowing it to infect the computer. Kaspersky Lab products detect this type of legitimate software (remote administration tools), but with a ‘not-a-virus’ verdict, displaying a yellow detection notification window. This is done in order to keep the user informed when remote access software is launched on a computer, because this type of software was used by Lurk operators without the victim’s knowledge or consent, and is still used by cybercriminals distributing other malware adapted to steal money.
As soon as we discovered that the Ammyy Group website had been breached and was distributing a malicious program, we reported it to the company’s representatives. After that, as Ammyy Group communicated, the site was checked, and the alien code was removed. In February, we notified the company of three such instances when malware was being distributed, and each time the problem was solved, although only temporarily.
Interestingly, on June 1 the content of the dropper changed. On that very day, it was reported that the creators of Lurk had been arrested, and the website began distributing a new malicious program, Trojan-PSW.Win32.Fareit, in place of Lurk; this new Trojan was also designed to steal personal information. This suggests the malicious actors behind the Ammyy Admin website breach are offering the chance to buy a place on their Trojan dropper in order to spread malware from ammyy.com.
We informed Ammy Group of the new attack and the new malware being distributed from the website ammyy.com.
Kaspersky Lab’s products proactively protect users from the installation of the malicious dropper program (as well as from the piggybacked programs Trojan-Spy.Win32.Lurk and Trojan-PSW.Win32.Fareit), and block it from being downloaded from the website ammyy.com.
MD5
D93B214C093A9F1E07248962AEB74FC8
FA3F9938845EC466993A0D89517FE4BD
C6847F43C3F55A9536DDCD34B9826C67
5811244C03A0A074E56F44B545A14406
EF231C83CA2952B52F221D957C3A0B93
CFD5093CB2BB3349616D9875176146C1
2F3259F58A33176D938CBD9BC342FDDD
186789B35DFCDFEBFE7F0D4106B1996F
E483C477F78119AF953995672E42B292
B084C2099CE31DD8D3E9D34F31CD606D




















Lurk: a danger where you least expect it