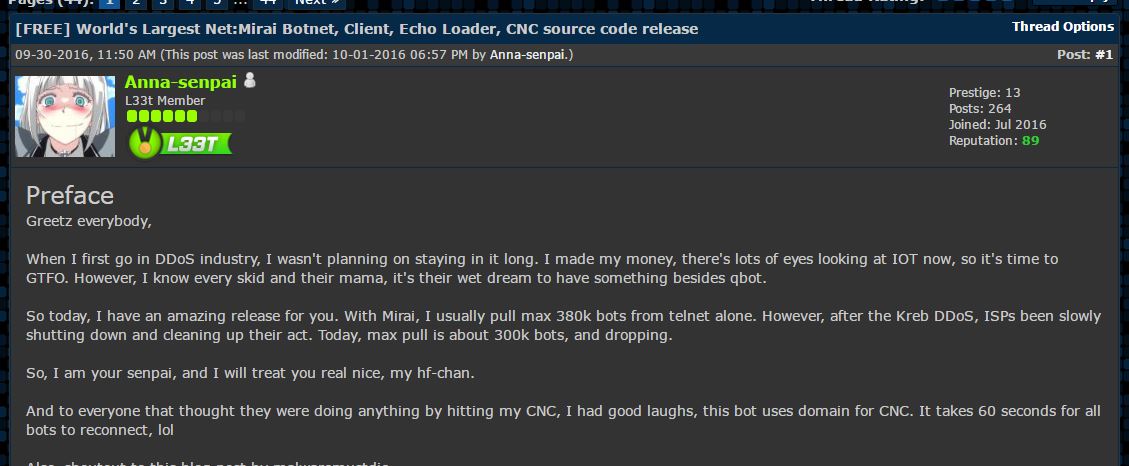
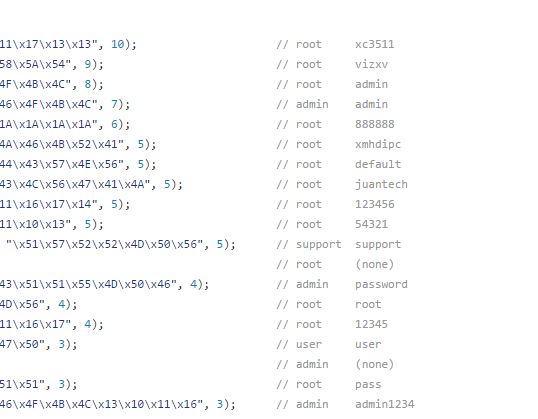
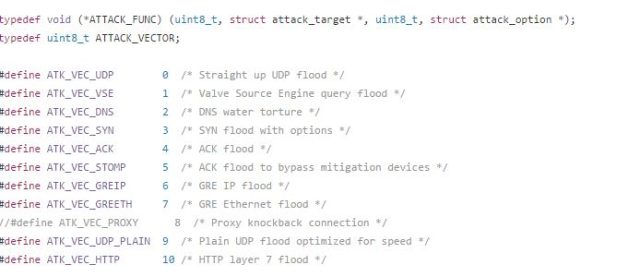
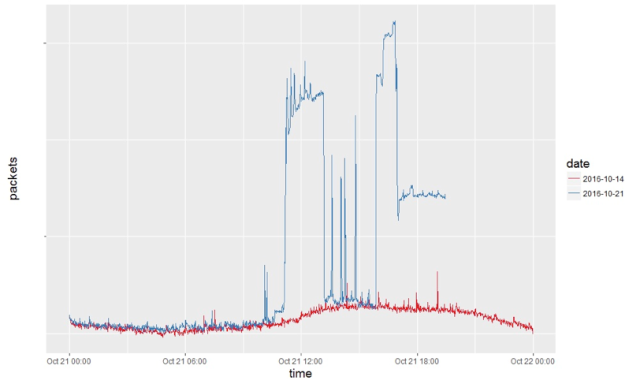
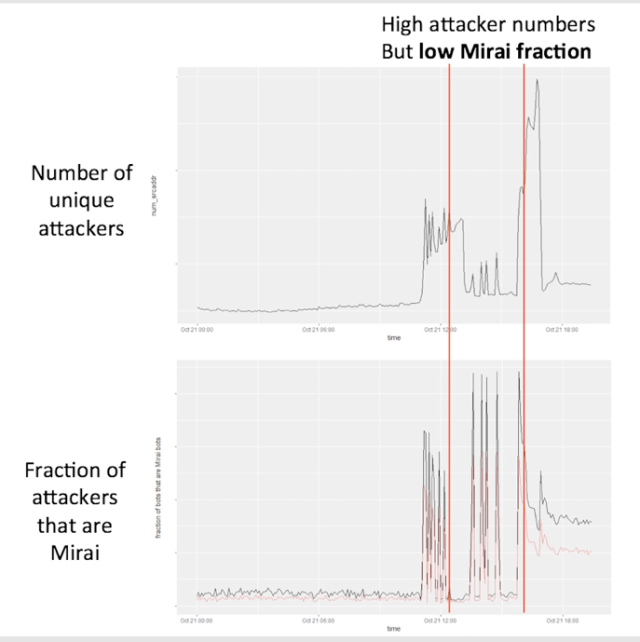
Welcome to the Internet of Evil Things. The attack that disrupted much of the Internet on October 21 is still being teased apart by investigators, but evidence thus far points to multiple "botnets" of Internet-connected gadgets being responsible for blocking access to the Domain Name Service (DNS) infrastructure at DNS provider Dyn. Most of these botnets—coordinated armies of compromised devices that sent malicious network traffic to their targets—were controlled by Mirai, a self-spreading malware for Internet of Things (IoT) devices.
But other systems not matching the signature of Mirai were also involved in the coordinated attack on Dyn. "We believe that there might be one or more additional botnets involved in these attacks," Dale Drew, CSO of Level 3 Communications, told Ars. "This could mean that they are 'renting' several different botnets to launch an attack against a specific victim, in which multiple other sites have been impacted."
The motive may have been blackmail, with the attacker seeking a payout by Dyn to stop. [Update: Dyn has said there was no financial motivation behind the attack.] But Drew warned that the huge disruption caused by the attack "could result in large copycat attacks, and [a] higher [number of] victim payouts [so] as to not be impacted in the same way. It could also be a signal that the bad guy is using multiple botnets in order to better avoid detection since they are not orchestrating the attack from a single botnet source."
Mirai has played smaller roles in previous attacks. It factored into last month’s extended distributed denial of service (DDoS) attack on the website of information security reporter Brian Krebs and an even larger DDoS against the French cloud provider OVH. Mirai clearly was the star of the attack on Dyn, apparently controlling multiple groups of bots.

 Loading comments...
Loading comments...
