The operator of at least one website has been spotted using small windows hidden under the user's Windows taskbar to continue to operate an in-browser miner even after the user closed the main browser window.
Discovered by Malwarebytes researcher Jerome Segura, the miscreants behind this campaign utilize a tactic known as a pop-under, a trick that allows them to spawn a new window, separate from the main browser.
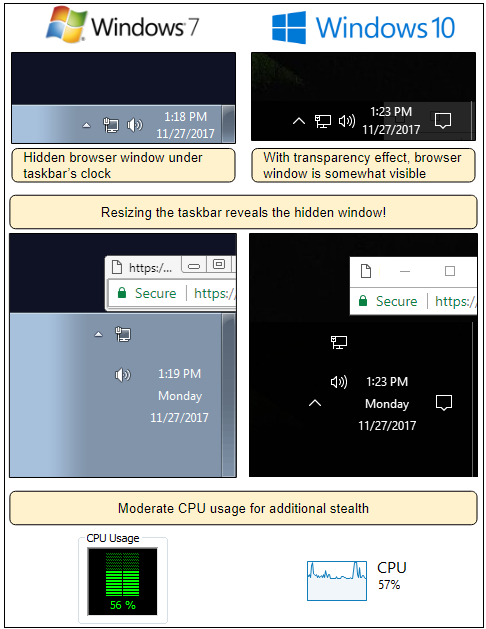
Site operator hid popup under Windows taskbar
JavaScript code also allows the abusive website owners to configure the size of this window and its coordinates (position) on the user's screen.
According to Segura, this website — an adult portal— used the following formula to dynamically calculate the position of this new window.
Vertical position = (current screen height) – 40px
For most users, this would display a tiny window hiding under the Windows taskbar. Crooks would then load a JavaScript file inside this hidden window. This file is a customized version of the Coinhive in-browser miner, a script that would utilize the user's CPU resources to mine the Monero cryptocurrency for the crooks.
Popup is hard to spot but fairly easy to remove
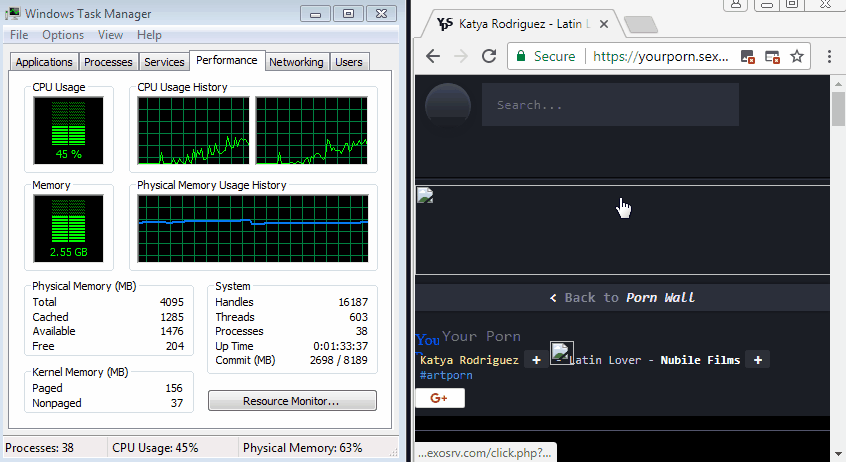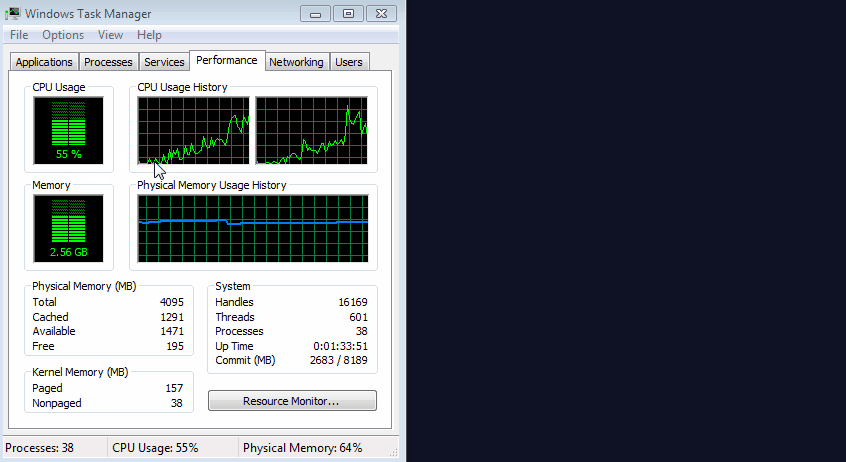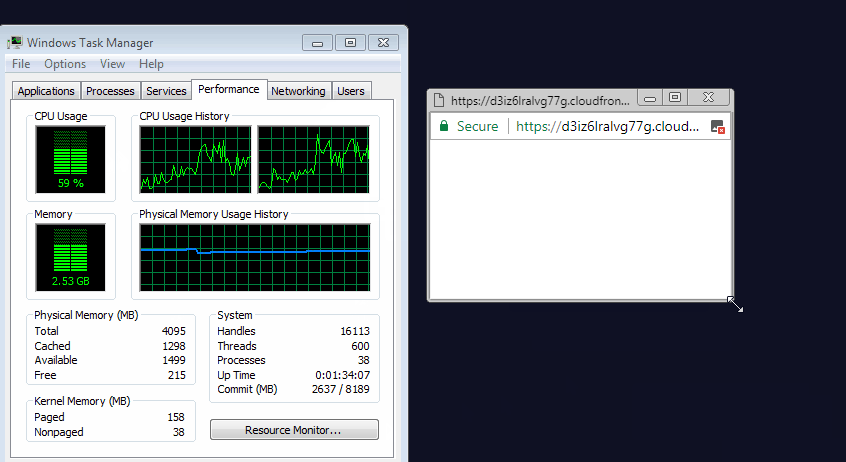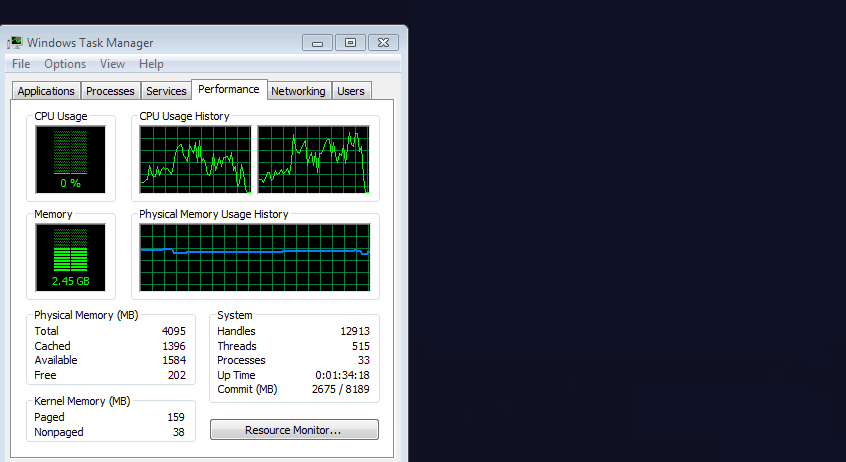
Unless users have transparency enabled with their OS interface, they would have no chance at spotting this hidden window, unless they went looking for rogue processes inside the Windows Task Manager.
Furthermore, unlike most other cryptojackers, the script does not utilize the user's full CPU power, but limits its activity to lower values, hoping not to induce a slowdown of the user's computer.
According to Segura, if users spot something wrong, they can use the Windows Task Manager to kill the rogue browser process associated with this window, or resize the Windows taskbar and force the window to become visible.
Trick spotted on one site —for now
At the time of writing, this technique appears to work only with Chrome browsers and has been spotted just on one single site —yourporn[.]sexy.
Malwarebytes said in a report released earlier this month that its security product blocks 8 million requests to cryptojacking services on a daily basis. Most security products and ad-blocking browser extensions come with support for blocking in-browser miners.
Bleeping Computer has tracked most major cryptojacking events since mid-September when these types of attacks became trendy (again) after the launch of the Coinhive service.
In the early 2010s, when Bitcoin mining was still profitable, US authorities stepped in to shut down a similar service called Tidbit.
Here's previous legal precedent where a former in-browser (Bitcoin) miner was shut down by US authorities https://t.co/4WdbRnHsmx pic.twitter.com/q8j0y85o3D
— Catalin Cimpanu (@campuscodi) November 25, 2017
This article was based on a Malwarebytes investigation provided to Bleeping Computer ahead of publication. We will update our story with a link to Malwarebytes' detailed report once it is available on the company's official website. UPDATE: The report is now live here.


Comments
Occasional - 6 years ago
As mentioned, not a new tactic; it's just applied to a new agenda.
I still wonder if browser vendors have been slow to offer safeguards against window manipulation, because of pressure from those sites that use it for, at least somewhat, less dishonest agendas.