Ethical hackers are warning businesses who use Amazon S3 cloud storage if they have left data exposed for anyone to access... by leaving "friendly warnings" on the servers.
Making sensitive data available to unauthorised users on unsecured Amazon's cloud-based AWS storage servers (known as "buckets") is nothing new. Well-known organisations such as FedEx, Verizon, and even The Pentagon have made the mistake of leaving private information exposed on unprotected Amazon data repositories.
All indications suggest that those reports are just the tip of the iceberg, and many more firms are putting themselves, their partners, and innocent members of the public at risk through careless data security.
This hasn't, of course, gone unnoticed by members of the computer security community - some of whom are using some eyebrow-raising techniques to raise awareness of the problem.
In an ideal world, a legitimate security researcher would contact a company directly and tell them that they have left their Amazon S3 bucket unsecured by not setting the right access permissions. However, there is always the fear that a company might respond badly to the tip-off, and may even threaten a whistleblower with legal threats or by labelling them as a malicious hacker.
And that's why, as BBC News reports, some researchers may prefer to leave a "friendly" message on an unsecured Amazon S3 bucket, warning that a malicious hacker could exploit the access to do harm.
"The BBC found almost 50 warnings posted to the firm's servers. Many had more than one warning uploaded to them. The messages urged owners to secure their information before it was stolen by malicious hackers."
Ethical hacker Victor Gevers, posted a tweet containing a screenshot of a message he had found in an unsecured Amazon S3 bucket which (he was at pains to point out) had not been left by him:
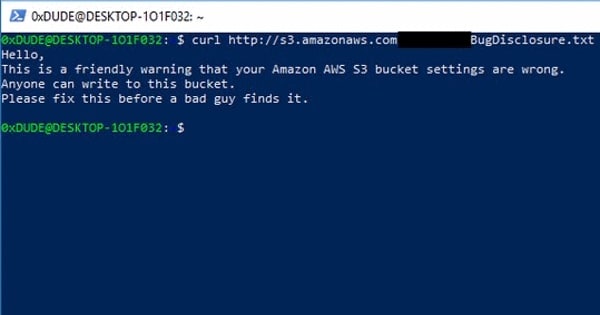
Hello,
This is a friendly warning that your Amazon AWS S3 bucket settings are wrong.
Anyone can write to this bucket.
Please fix this before a bad guy finds it.
Security researcher Chris Vickery, who has uncovered many examples of companies leaving unsecured databases on cloud storage buckets, says that he has seen similar warnings left for the last 6-12 months.
The very real fear, of course, is that it's not just ethical researchers who might spot the unsecured data buckets - there's every reason to believe that malicious hackers could exploit them too.
After all, it's only a year since there was a widespread attack against tens of thousands of unprotected MongoDB databases, when hackers wiped data from servers and left ransom demands. If left unprotected, Amazon S3 buckets could fall to a similar fate.
Last November, Amazon announced it was introducing more visible warnings on server administrators' dashboards that their buckets had been left publicly accessible. The warnings take the form of a bright orange "pill" on the admin user interface.
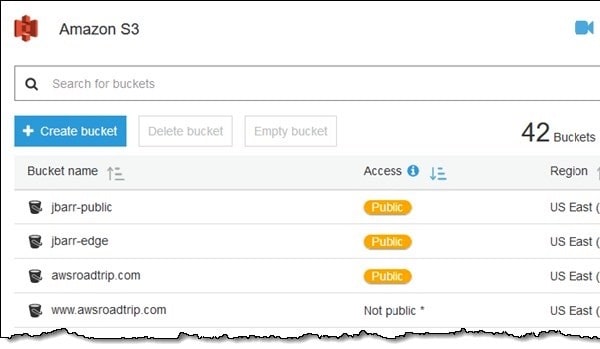
This week Amazon went further, saying that it was making its S3 Bucket Permissions check freely available to all customers, a feature which identifies buckets that are "publicly accessible due to ACLs or policies that allow read/write access for any user."
Previously the S3 Bucket Permissions check was only available to customers who had opted for Amazon's business and enterprise support plans.
Amazon's later announcement followed closely on media reports of Buckhacker, a tool which is effectively a search engine for information left publicly available on Amazon S3 buckets.





