
If you’re using an Android device—or in some cases an iPhone—the Telegram messenger app makes it easy for hackers to find your precise location when you enable a feature that allows users who are geographically close to you to connect. The researcher who discovered the disclosure vulnerability and privately reported it to Telegram developers said they have no plans to fix it.
The problem stems from a feature called People Nearby. By default, it’s turned off. When users enable it, their geographic distance is shown to other people who have it turned on and are in (or are spoofing) the same geographic region. When People Nearby is used as designed, it’s a useful feature with few if any privacy concerns. After all, a notification that someone is 1 kilometer or 600 meters away still leaves stalkers guessing where, precisely, you are.
Stalking made simple
Independent researcher Ahmed Hassan, however, has shown how the feature can be abused to divulge exactly where you are. Using readily available software and a rooted Android device, he’s able to spoof the location his device reports to Telegram servers. By using just three different locations and measuring the corresponding distance reported by People Nearby, he is able to pinpoint a user’s precise location.
Telegram lets users create local groups within a geographical area. Hassan said that scammers often spoof their location to crash such groups and then peddle fake bitcoin investments, hacking tools, stolen social security numbers, and other scams.
“Most users don't understand they are sharing their location, and perhaps their home address,” Hassan wrote in an email. “If a female used that feature to chat with a local group, she can be stalked by unwanted users.”
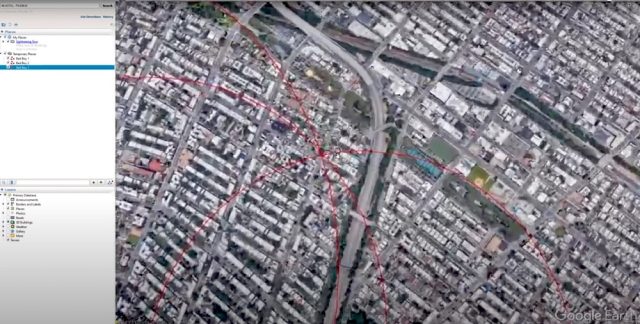
A proof-of-concept video the researcher sent to Telegram showed how he could discern the address of a People Nearby user when he used a free GPS spoofing app to make his phone report just three different locations. He then drew a circle around each of the three locations with a radius of the distance reported by Telegram. The user’s precise location was where all three intersected.
Hassan asked that the video not be published. The screenshot below, however, gives the general idea.
Fixing the problem
In a blog post, Hassan included an email from Telegram in response to the report he had sent them. It noted that People Nearby isn’t enabled by default and that “it's expected that determining the exact location is possible under certain conditions.”
Telegram representatives didn’t respond to an email seeking comment.
People Nearby poses the biggest threat to people using Android devices, since they report a user’s location with enough granularity to make Hassan’s attack work. The recently released iOS 14, by contrast, allows users to divulge only a rough approximation of their location. People who use this feature aren’t as exposed.
Fixing the problem—or at least making it much harder to exploit it—wouldn’t be hard from a technical perspective. Rounding locations to the nearest mile and adding some random bits generally suffices. When the Tinder app had a similar disclosure vulnerability, developers used this kind of technique to fix it.
The privacy consequences of Telegram’s People Nearby feature are a good reminder that features can often be abused in ways that aren’t contemplated by the people who develop them. Users who want to keep their whereabouts private should be suspicious of location-based services and do research before installing or turning them on.
reader comments
92